Why it matters: Everyone loves the convenience of contactless payments, especially when you are in a hurry. However, this convenience often comes at the cost of reduced security. It turns out that a combination of flaws in both Apple Pay and Visa's system can allow a hacker to make unauthorized payments using only a stolen, powered on iPhone.
A group of researchers at the Birmingham and Surrey Universities in the UK have revealed a new iPhone flaw that allows attackers to perform unauthorized contactless payments by exploiting a weakness in Apple Pay's Express Transit feature while using a Visa card.
Express Transit (Express Travel in the UK) allows an iPhone user to tap-and-go at ticket barriers for much quicker payments. In other words, it eliminates the need to authenticate using either a passcode, Touch ID, or Face ID when making payments, but this also introduces a weakness that can easily be exploited with a relatively inexpensive piece of commercially available radio equipment.
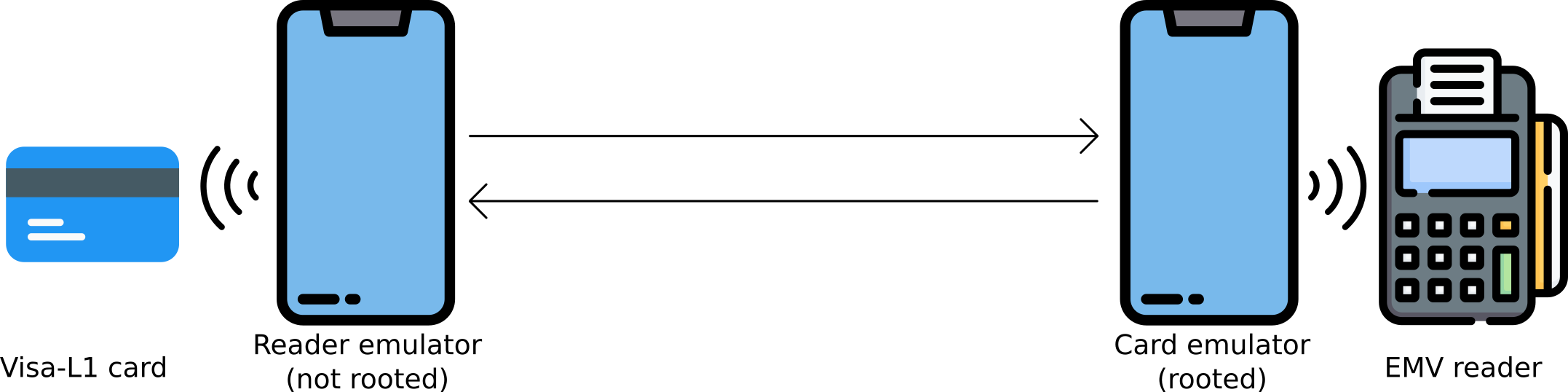
The researchers explained that all it takes to make an unauthorized contactless payment of £1,000 (around $1,350) is to program the radio equipment to mimic a ticket barrier system and relay so-called "Magic Bytes" through an Android app in order to emulate a real contactless transaction. Dr. Ioana Boureanu, who is one of the researchers who discovered the vulnerability, says the dummy payment terminal and Android phone need to be near the victim's iPhone for the exploit to be successful, which becomes painfully easy in the case of a lost or stolen iPhone.
So far, the researchers haven't found any evidence that this security flaw has been exploited in the wild, but lead researcher Dr. Andreea Radu believes it's only a matter of time before malicious actors will take advantage of it. Apple was notified about the issue in October 2020, but the company passed the responsibility to Visa, who was notified in May 2021. The latter says it's familiar with countless variations of contactless fraud schemes developed in the lab and maintains the exploit is "impractical to execute at scale in the real world."
As of writing, neither company is willing to provide a fix. Visa claims you'll be protected under its zero liability policy, and the researchers say they haven't found the same issue when testing Express Transit with Mastercard. Additionally, when trying the same attack method with Samsung Pay, the researchers found that while transactions are possible with locked Samsung devices, the transaction value is zero and the approval process is based on a special arrangement between the bank and the transport providers on the exact cost of the tickets.
For now, if you want to be extra safe, you can disable Express Transit payments. If you're looking for an in-depth read on the matter, you can find the associated research paper here. You can also check DinoSec's extensive list of lock screen bypass issues affecting each major iOS version since iOS 5.
