What just happened? Once again, the Google Play Store has been caught hosting malware-loaded malicious apps. The culprit in this instance was able to steal cryptocurrency by tricking users into depositing it in attackers' wallets.
For those who don't know, addresses of crypto wallets consist of long strings of characters. Rather than typing them out, most people copy and paste them using the Android clipboard---something that "clipper" malware uses to its advantage. It simply replaces the copied wallet address with one of its choosing, resulting in victims depositing digital currency into the attackers' wallets instead of the intended locations.
Clipper malware isn't new; it was discovered on Windows back in 2017 and on sketchy Android app stores last year. But this is the first time it has been identified on the official Google Play Store.
Researchers from security firm ESET found that the malicious app disguised itself as a cryptocurrency application called MetaMask. While this is a legitimate service for running distributed Ethereum apps, MetaMask only offers add-ons for popular browsers; it does not have a mobile application.
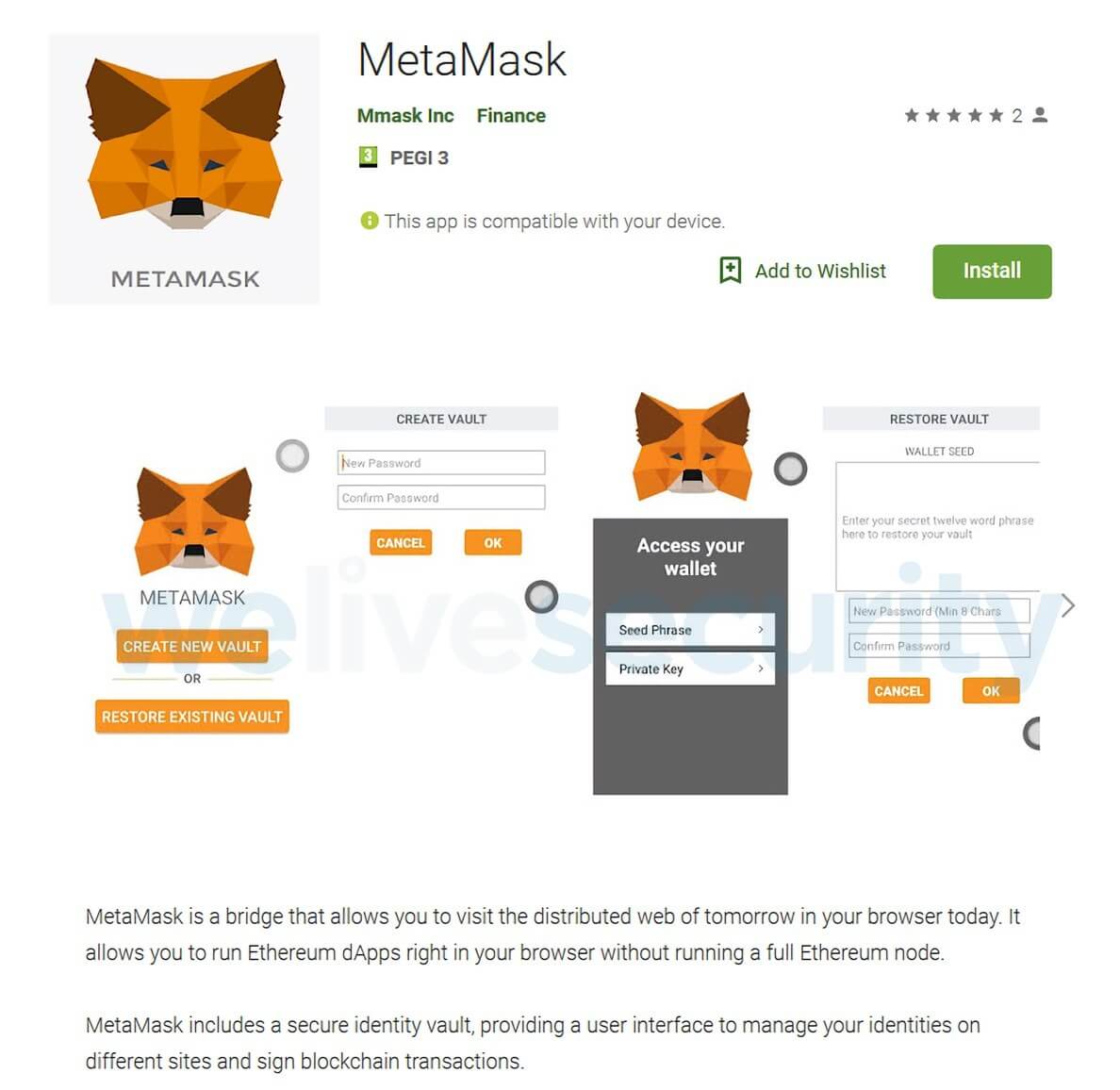
The fake MetaMask app arrived on the Play Store on February 1. It was removed soon after ESET informed Google of its presence. No mention of how many times it was downloaded, but it doesn't appear to have infected a huge number of users.
Earlier this month, a batch of malware-laden apps were found on the Play Store. While these type of programs aren't often installed in large numbers, the 29 applications in this instance were downloaded 4 million times.
