PSA: If you own an iPhone running iOS 17 or any Android or Windows device and notice strange behavior, such as connection pop-ups from out of the blue or random rebooting, turn off your Bluetooth. Hucksters are using Flipper Zeros to disrupt phones and computers in public areas. Currently, there is no fix other than temporarily shutting down Bluetooth reception.
Infosec researcher Jeroen van der Ham recently stumbled upon an iPhone vulnerability while riding the train in the Netherlands. During the trip, his iPhone 15 began popping up Apple TV connection notifications. Shortly after, the phone rebooted itself. The trouble continued and wouldn't stop even after he put the phone in Apple's Lockdown mode. It finally stopped after he got off the train.
On his return trip, it happened again, and being more alert this time, he noticed it wasn't just him. Almost everyone in the train car was having trouble with their iPhones rebooting--all save for one guy working on a laptop. He had his iPhone plugged into the computer, but it was not rebooting or showing notifications.
Van der Ham finally confronted the man and told him to knock it off.
"Amazing coincidence, this person happens to be in the same carriage on my way back," Van der Ham related on Mastodon. "I recognized him and asked him to stop f***ing around because it is extremely annoying."
He complied, and Van der Ham noticed the man had a Flipper Zero in his pocket, causing the denial of service disruption.
Flipper Zero is a radio device that does a multitude of things. It supports RFID, NFC, WiFi, and Bluetooth protocols and can even operate on standard radio frequencies. It is intended for admins to easily perform penetration testing on things like employee badge readers and similar radio-based entry points. Performing these tests can be complicated and require expensive specialized equipment. Conversely, Flipper Zero costs about $200, so it's a handy and inexpensive tool.
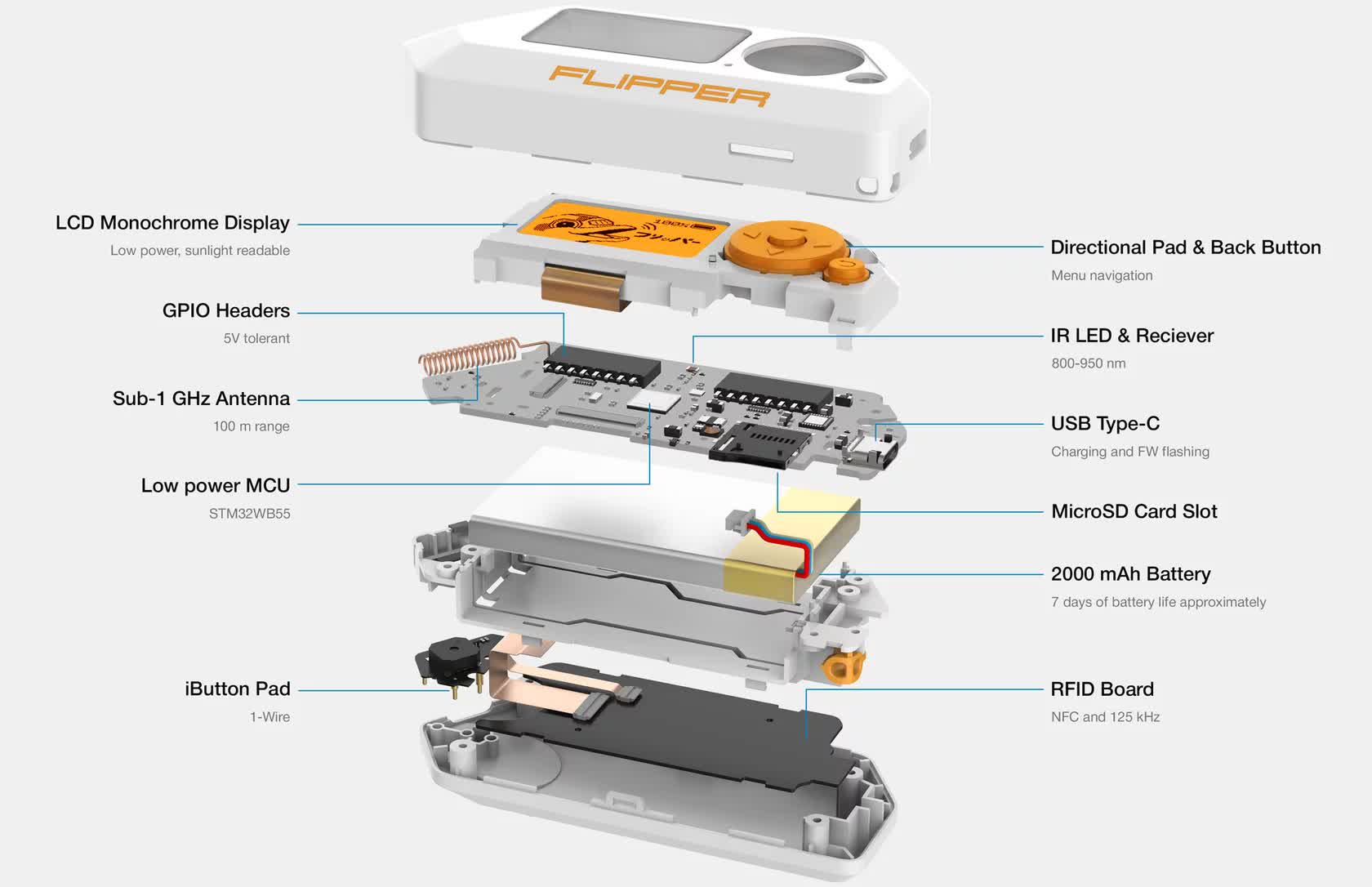
Unfortunately, bad actors can use it to cause trouble, like cloning hotel keys, opening garage doors, or skimming credit cards. This caveat is partly why Amazon banned the device in April of this year.
After the train incident, Van der Ham conducted tests using a Flipper Zero. Instead of using the stock firmware, he flashed it with a custom package called Flipper Extreme. It is one of many customized software for the device you can find online. He found that one on a Flipper Zero Discord channel.
Flipper Extreme has a feature that sends a constant stream of BLE connection requests to all nearby devices. It also has a setting that targets iOS 17 specifically, which is what the guy on the train was using. Van der Ham successfully recreated the DoS attack he experienced on the train.
However, it only works for iOS 17 or later. The only iPhone running iOS 17 by default is iPhone 15, but owners of iPhone X or iPhone SE second generation or later can manually install iOS 17. So, if you haven't upgraded yet, you might want to hold off until Apple has a fix. It is unclear if Apple is even aware of the issue, as it has not responded to requests for comment.
For now, the only known mitigation is to turn off Bluetooth in settings completely. Ars Technica notes that using the Control Center (diagonal swipe down from the right corner of the screen) and using the button to disable Bluetooth temporarily doesn't prevent the attack.
Android and Windows users are not immune to this type of attack either. While the Flipper Extreme iOS attack is specific to iOS 17, the firmware can just as easily disrupt Android phones or Windows platforms using its standard BLE continuous hail option, as illustrated by the video above.
To mitigate on Android, find "nearby share" in settings and toggle off "show notification." For Windows, go to Bluetooth settings and uncheck "Show notifications to connect using Swift Pair."
This vulnerability is more a nuisance than a threat. Hackers cannot use it to access your device or information. It just makes operating it a pain in the rear. If you don't expect to use Bluetooth when you are out in public, turn it off beforehand, as trying to switch it off during an active attack could be difficult.
