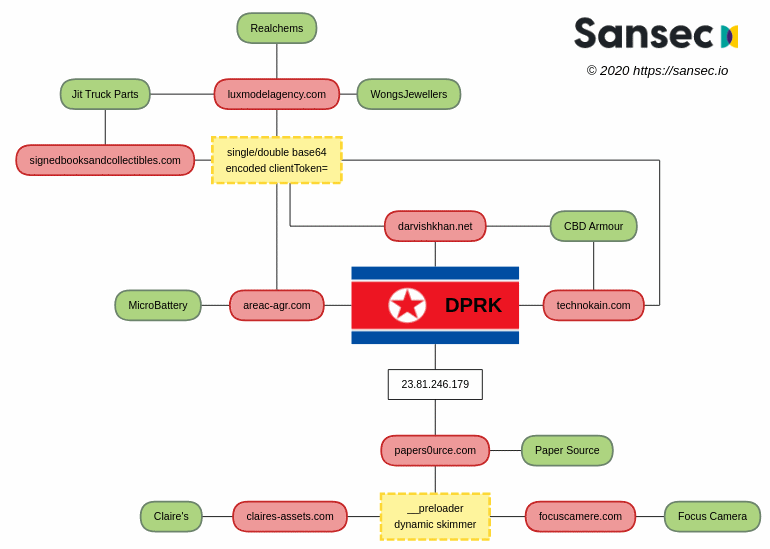
Why it matters: Hackers associated with the notorious North Korean Lazarus Group are breaking into online stores and stealing customers' card details when they visit the checkout page. The attacks, known as 'web skimming' or 'Magecart attacks' have been going on since May 2019 and have hit large retailers such as international fashion chain Claire's.
The attacks were reported by Dutch cyber-security firm SanSec (via ZDNet). It writes that the digital skimming technique has been growing since 2015, and while it was traditionally used by Russian- and Indonesian-speaking hacker groups, government-sponsored North Korean criminals are now intercepting credit card details from online stores.
The attacks involve gaining access to a web store's backend server, often achieved by using booby-trapped emails (spearphishing) sent to employees to obtain their passwords. The hackers infiltrated the site of accessory store Claire's in April and June.
Once a site is compromised, the malicious script loads on the checkout page, stealing credit card details as they're entered into the forms. Once the transaction is completed, the intercepted data is sent to a collection server controlled by the hacking group and sold on the dark web.
The group developed a global exfiltration network to monetize the skimming operations. This involved hijacking and repurposing legitimate sites to serve as disguises for the criminal activity and funnel stolen assets. A modeling agency from Milan, a vintage music store from Tehran, and a family-run book store from New Jersey were all part of the network.
Sansec researchers found links between the skimming activity and previous North Korean hacking operations. The evidence points to Hidden Cobra, aka the Lazarus Group, which was behind the 2014 Sony Pictures hack, the heist on a Bangladeshi bank in 2016, and is widely believed to have been responsible for the WannaCry malware.