Forward-looking: Intel is baking new anti-malware protections into its latest mobile CPUs, as well as upcoming desktop and server platforms. The new CPU-level security feature is called Control-Flow Enforcement Technology (CET), meant to protect against classes of malware that so far have been difficult to mitigate only via software.
Intel's CET will first become available with Tiger Lake mobile CPUs that are expected to drop in the second half of 2020. So far we've seen a few Tiger Lake ULV variants popping up here and there, and we know they'll offer PCIe 4.0 and USB 4.0 support, along with some other niceties in the GPU department. The fact that it'll also have better security is a nice bonus on top of all that.
Intel says it's been working on CET since 2016, when it first revealed official specifications so that Microsoft and other parties could have time to adopt it in software. CET brings to the table two new capabilities called Shadow Stack and Indirect Branch Tracking.
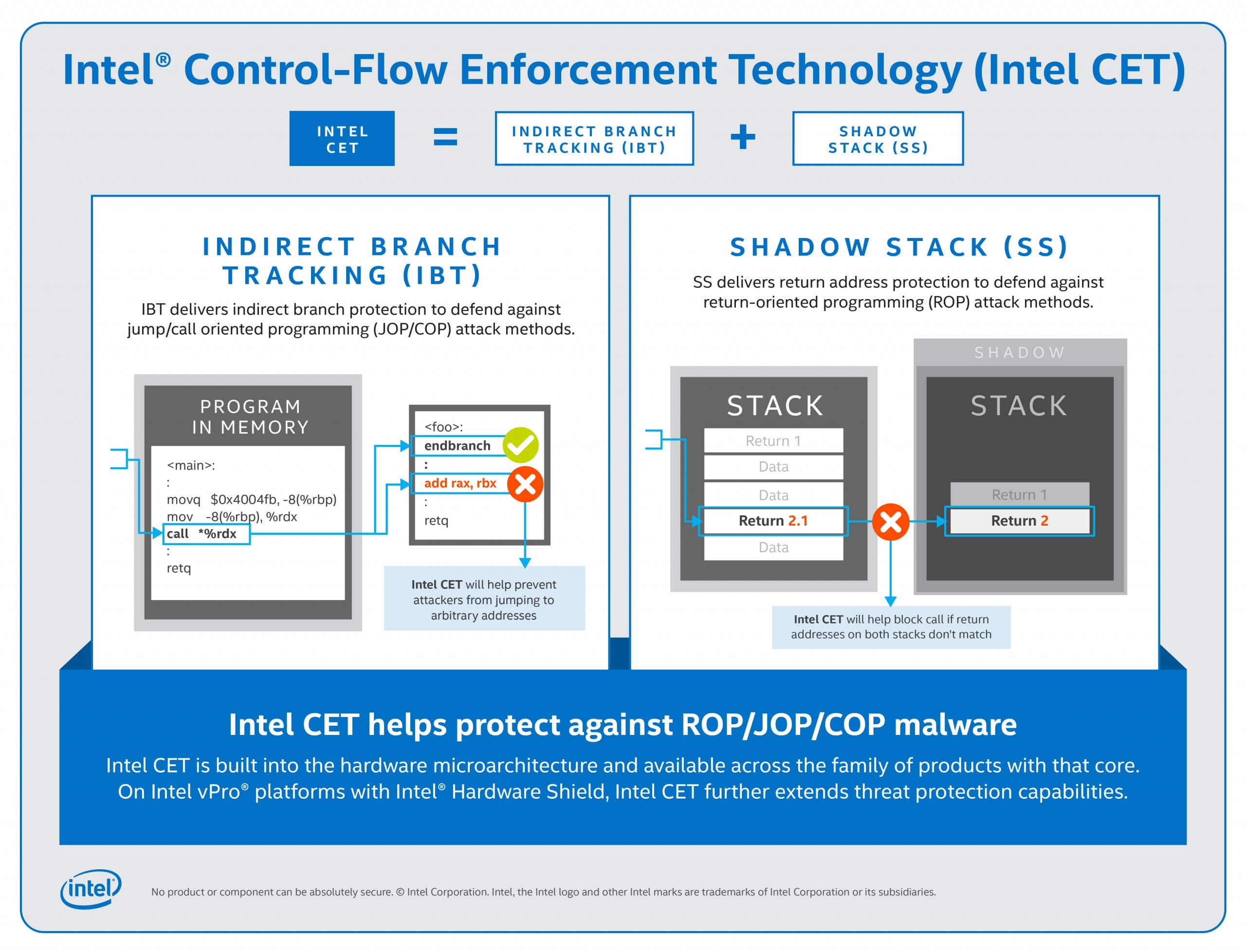
Malicious actors often use Call Oriented Programming (COP), Jump Oriented Programming (JOP), or Return Oriented Programming (ROP) to bypass standard anti-malware protection. These techniques use code from executable memory to change an app's behavior, so they require more advanced detection and mitigation methods.
Shadow Stack allows the CET's state machine to detect and block attempts from a malicious program by flagging mismatches between the address of the 'shadow' and that of the attacked program. Then CET uses Indirect Branch Tracking so that the target software can block JOP and COP attacks.
Intel says that vPro platforms already meet the security requirements of secured-core PCs, however CET is meant to offer an additional layer of protection for both enterprise and consumer-grade systems. The timing couldn't be better, as vulnerabilities in Intel CPUs keep making news since Meltdown and Spectre hit them hard in early 2018.