A hot potato: Just when you thought that Intel's largely undocumented CPU master controller didn't have any more flaws, two more have been revealed by security researchers at three universities. On a positive note, this time the issues are fixable and there's no evidence the new vulnerabilities have been exploited in the wild.
Security researchers revealed details about a new vulnerability in Intel processors that allows hackers to take advantage of the way multi-core architecture works in order to grant access to sensitive data on compromised systems. The findings were published by academics at the University of Michigan, the VU University of Amsterdam, and the University of Adelaide in Australia, who produced proof of concepts for two different attack methods dubbed SGAxe and CrossTalk.
The first appears to be an advanced version of the CacheOut attack revealed earlier this year, in which hackers could extract contents from the CPU's L1 cache. Researchers explain that SGAxe is a result of Intel's failed attempts at mitigating side-channel attacks against Software Guard Extensions (SGX), which is the dedicated area of a CPU that's supposed to ensure the integrity and confidentiality of code and data that is being processed.


By using a "transient execution attack," an attacker can essentially recover the cryptographic keys stored in SGX, which are then used to "decrypt the long term storage of the quoting enclave, obtaining the machines EPID attestation keys." Attestation keys are used to protect the security of things such as financial transactions and DRM-protected content.
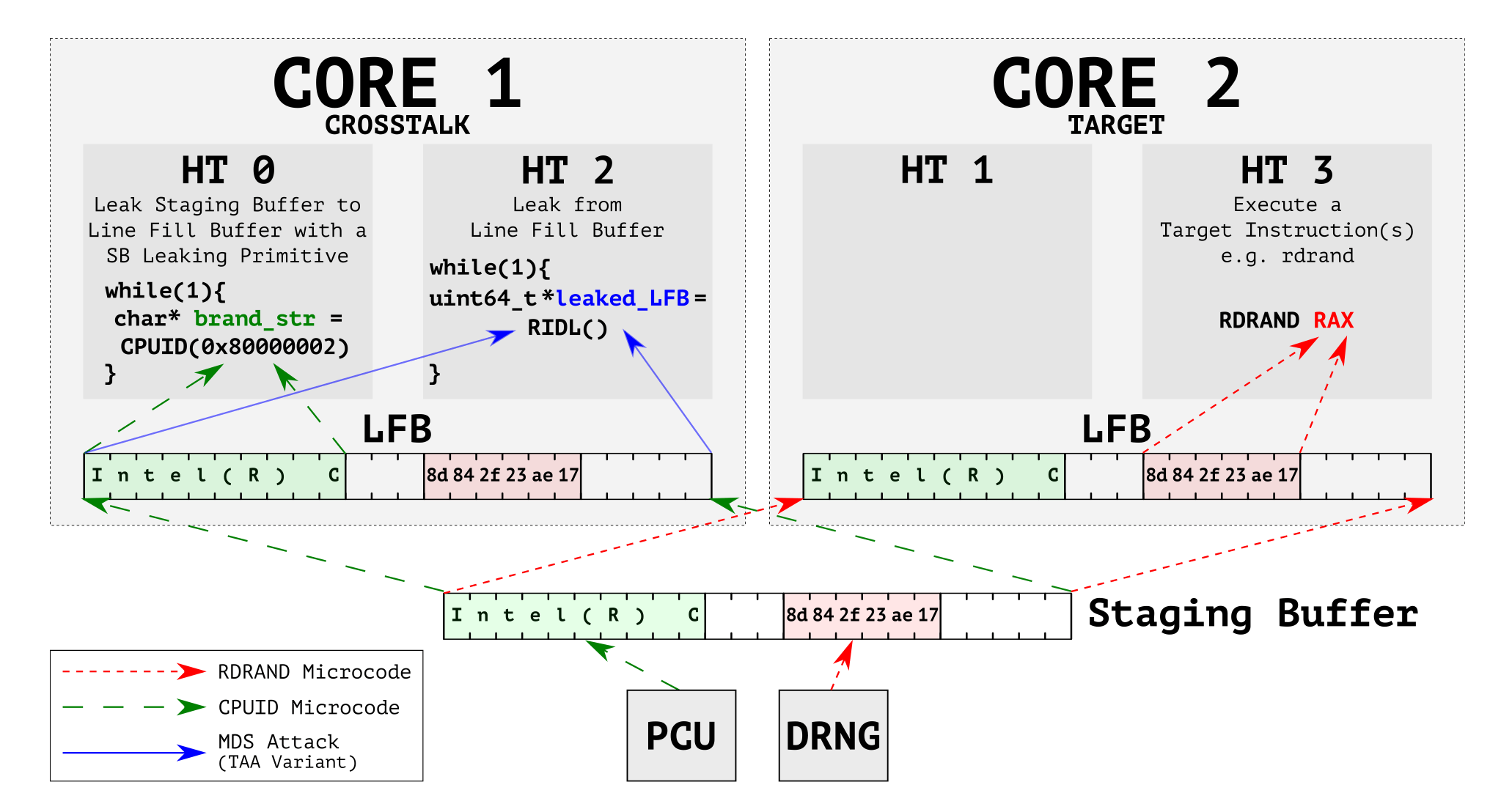
The second attack is of the Microarchitectural Data Sampling (MDS) variety and can be performed against data that is being processed by the CPU's Line Fill Buffer (LBF). The idea here is that by exploiting a "staging buffer" whose contents are accessible to all CPU cores, a hacker can use a specially crafted piece of software that runs on one core to compromise the private keys that guard the code and data of software running on a separate core.
The flaws affect several Intel CPUs released between 2015 and 2019, including some Xeon E3 (E5 and E7 have proven immune to the attacks). Intel said in its June security advisory that it's highly unlikely anyone would be able to perform these attacks outside of lab settings. The company will, however, release a microcode update as soon as possible and will also invalidate previously signed attestation keys.