A hot potato: Zoom recently got out of a messy situation where its iOS app was secretly sharing data with Facebook, but now another problem has reared its head that potentially affects user privacy on all platforms because of how the software's 'Company Directory' feature works.
Zoom's sky-rocketing popularity seems to be a mixed blessing for the company, as yet another privacy issue crept up this week, involving leakage of personal information of thousands of users by exposing their email address and photo to strangers on the platform and potentially enabling the latter to initiate unwanted video calls.
Also read: Zoom skyrockets to 200 million users, puts 90-day hold on features to address security flaws
The problem this time isn't confined to Zoom's recently fixed iOS app, but as Vice notes, is related to how the platform's "Company Directory" setting is configured. While users who've signed up with the same company email domain are grouped together to make searches and calls easier with colleagues, some people who used their private email to join Zoom have had thousands of strangers added to their contacts list, all of whom Zoom perceives are working under the same organization as they have the same domain name.
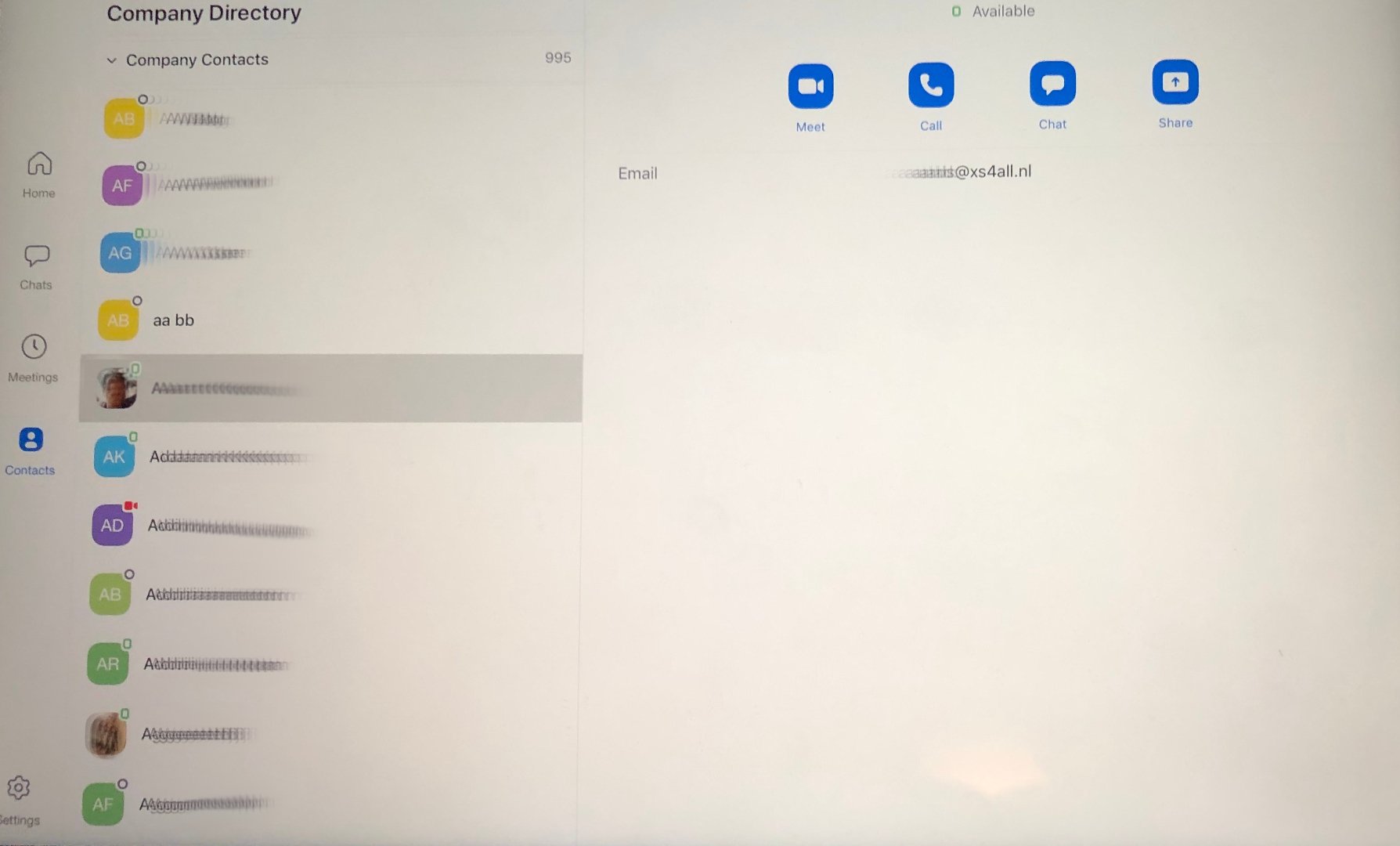
"If you subscribe to Zoom with a non-standard provider (I mean, not Gmail or Hotmail or Yahoo etc), then you get insight to ALL subscribed users of that provider: their full names, their mail addresses, their profile picture (if they have any) and their status. And you can video call them," said Barend Gehrels, a Dutch user who had 995 strangers added to his contacts list after signing up with an email domain from his local ISP.
Another user experiencing the same issue notified their ISP, who couldn't rectify it on their end and asked the complainant to contact Zoom. The company officially exempts the aforementioned public domains from a users' Company Directory but notes that they need to submit a request for manually blacklisting non-standard domains.
Zoom also blacklisted the specific domains highlighted by Vice in their report, but it remains to be seen how widespread the issue is for the millions of new users who've recently hopped on the platform for conducting remote meetings, taking online classes, and keeping in touch with their families.
Update: In addition to the aforementioned problem, it's been documented (as reported by Bleeping Computer) that because of how Zoom handles URLs in group chats, any URL you send/receive is converted into a hyperlink. However, this could be used maliciously, if instead of sending a web link, you receive a UNC path (Universal Naming Convention), this will also be converted to a link.
UNC paths are typically used for networking and file sharing (for example, \\127.0.0.1\C$\windows\system32\calc.exe). An unsuspecting user could click a malicious link, which would make Windows try to connect to a remote host using the Server Message Block (SMB) network file-sharing protocol. By default, Windows will send the user's login name and their NTLM password hash, which can be easily cracked.
Zoom has been contacted so they can issue a fix, so the chat client does not convert UNC paths into clickable links. There are also some workarounds available, but in short, don't go clicking any links you are sent via chat, let alone if it's not a trusted contact.
