A hot potato: Hot on the heels of a recently-discovered vulnerability in Intel's Converged Security and Management Engine, the security community has found yet another worrisome attack method that can be levied at x86 silicon used in millions of machines around the world. Researchers have discovered yet another flaw in Intel's CPU silicon that warrants a hardware redesign to fully solve the underlying issues. Called LVI, it's very similar to the Meltdown and Spectre vulnerabilities that were disclosed in 2018.
To put things in context, 2018 was the year when the infamous Meltdown and Spectre attacks were disclosed to the public. Meltdown allows hackers to access memory that should theoretically be inaccessible, while Spectre makes it easy to alter branch prediction structures in order to execute malicious code.
In a collaborative analysis made by Bitdefender and an academics team led by Jo Van Bulck, we get to see the complicated details of a new attack method that's potentially worse. It is called Load Value Injection (LVI), and it's part of a new class of attacks on Intel CPU's speculative execution.
This new method allows an attacker to take advantage of a feature present in most modern CPUs that can essentially achieve higher performance by guessing the future instructions that are likely to be thrown at it and preparing a set of results. Once the instructions are confirmed the wrong results are discarded.
Researchers were able to use LVI to do what is essentially Meltdown in reverse
LVI is something that an attacker can do to get your CPU to spit out the bits of data that should technically be securely stored through Intel's Software Guard Extensions (SGX). Pretty much any application that works with passwords, digital rights management, and encryption keys uses SGX to run code and keep data inside an isolated environment.
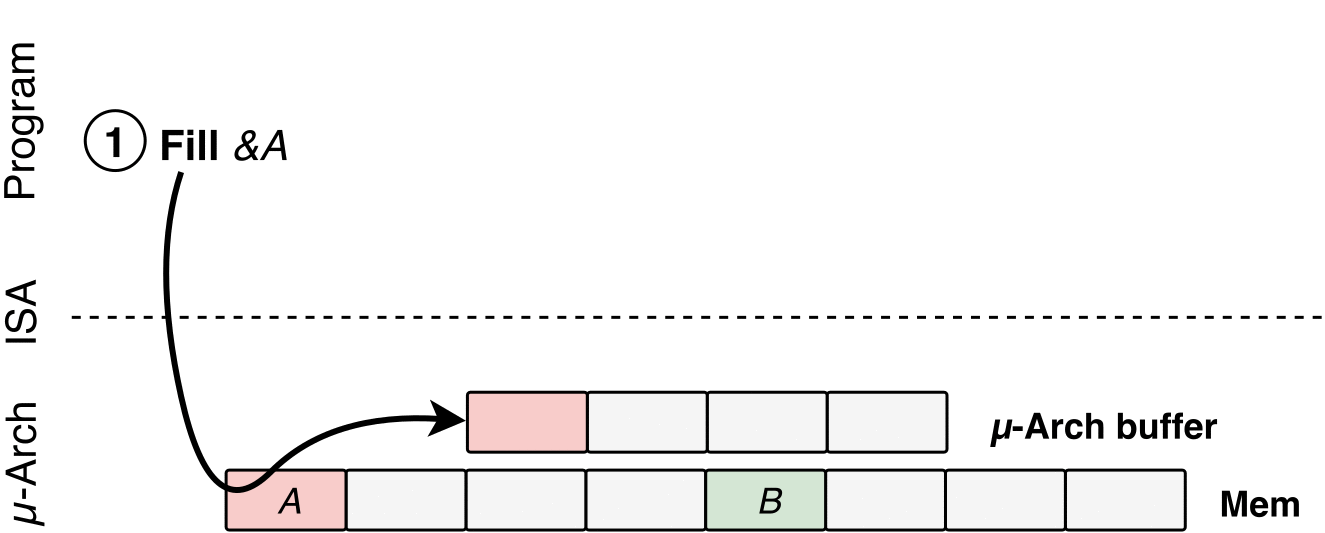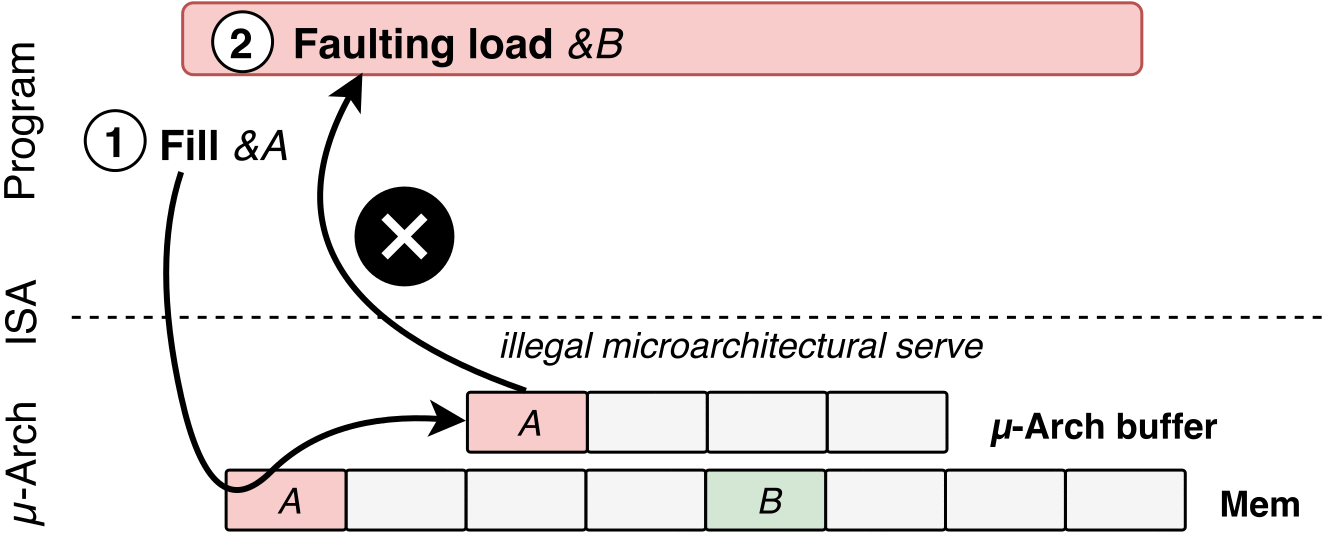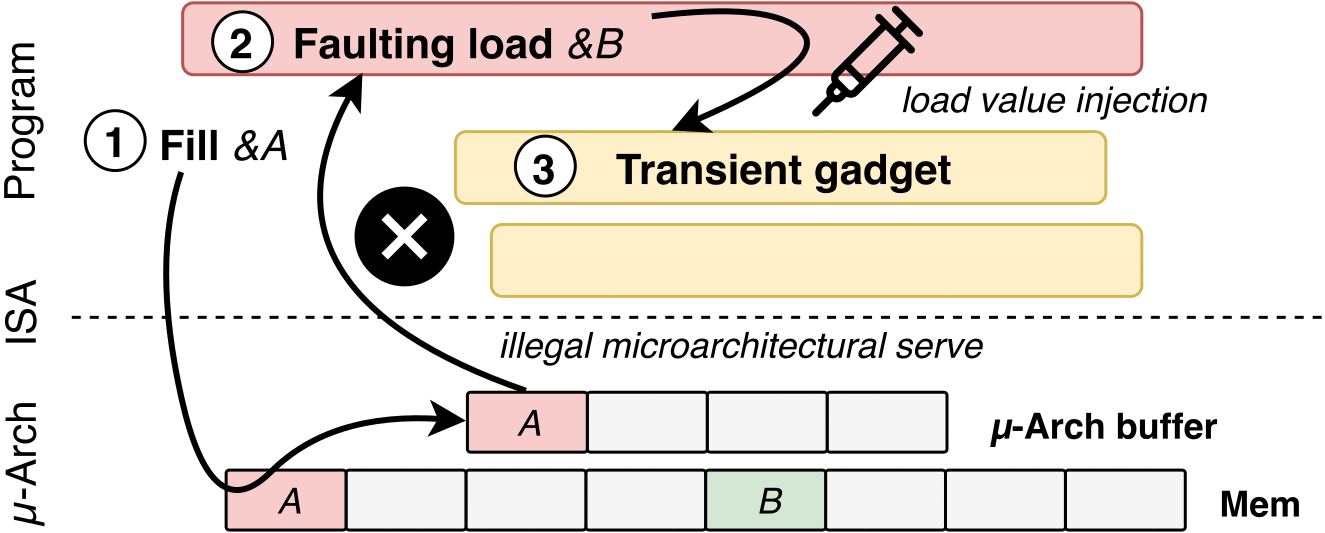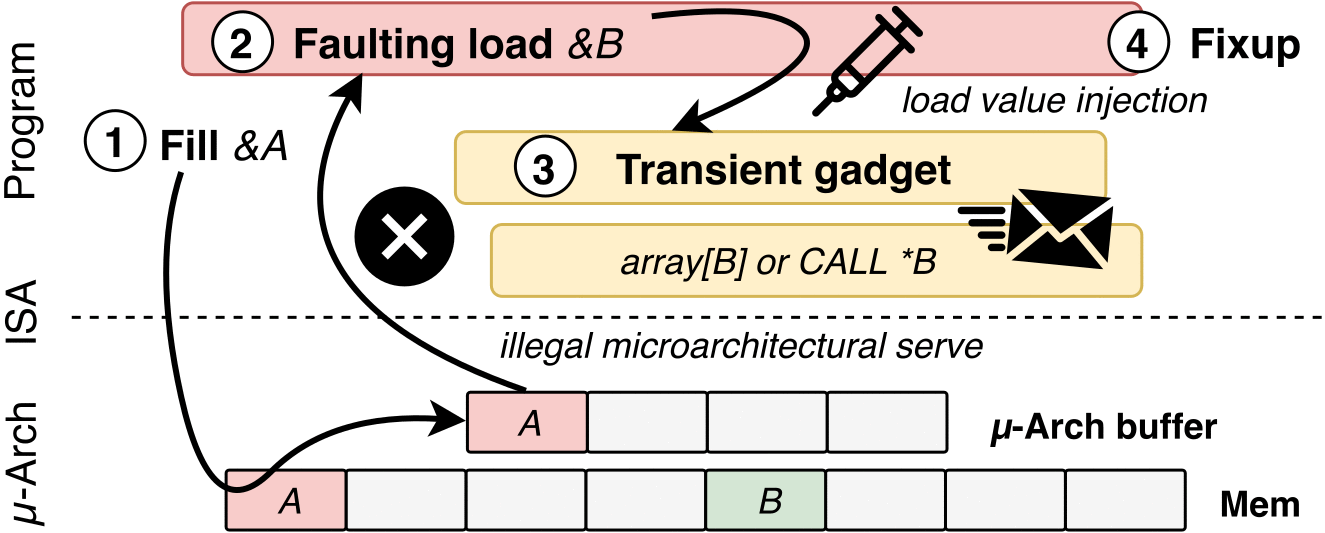
If your machine happens to have an OS or firmware vulnerability, SGX should normally compensate for that. Researchers were able to use LVI to do what is essentially Meltdown in reverse: they inject data to poison a hidden CPU buffer with custom data values that makes it easier to access data used by an app. From there, there's nothing stopping an attacker from gaining access to a higher-privileged process and achieving a broad impact on personal and work computers.
Bitdefender researchers explain that "this type of attack is particularly devastating in multi-tenant environments such as enterprise workstations or servers in the data center, where one less-privileged tenant would be able to leak sensitive information from a more privileged user or from a different virtualized environment on top of the hypervisor." Here it is in action:
The good news for you is that you probably shouldn't worry all that much, since this new attack method is more complex and a cloud environment would be a more suitable target. The list of affected processors includes an assortment of different models ranging from 4th-gen Xeons to 10th-gen Comet Lake Core CPUs. Interestingly, CPUs based on the Ice Lake architecture are not affected.
The bad news for enterprises is that they'll have to assess the risks and implement a number of software mitigations. Intel will supply microcode patches, but some organizations may also opt to disable features like hyper-threading in critical systems. Researchers also note that besides the expensive software patches needed, Intel's SGX enclave will run between 2 to 19 times slower as a result of the necessary mitigations.
For its part, Intel is downplaying the severity of LVI due to the sophistication level required to perform such an attack. The Bitdefender report seems to support that assessment, but Intel will still have to make improvements in its future silicon before malicious actors can come up with similar attacks that are more practical for real-world use.
In related news, AMD's CPUs have also been affected by a newly disclosed vulnerability that supposedly carries a similar severity level, though the company has heavily downplayed its importance.