In a nutshell: We know people still use terrible passwords, and that's a massive security risk. Companies are also at fault, with many using easily guessable default usernames and passwords in their devices---and hackers know it.
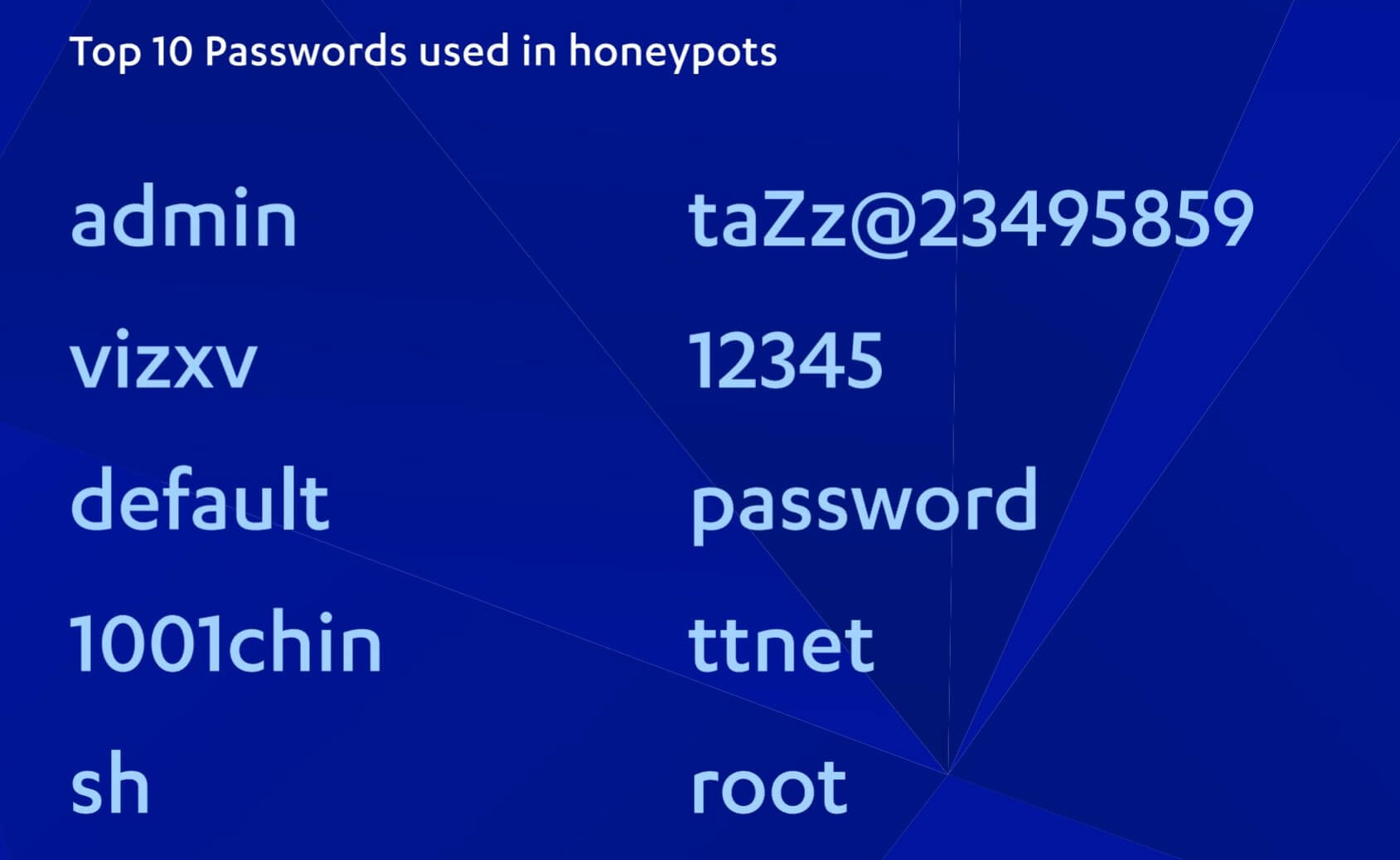
As a way of detecting patterns in cyberattacks, researchers from security company F-Secure set up a series of 'honeypot' decoy servers in countries around the world. Some of the most popular passwords that hackers tried appear in many worst passwords lists---"12345" and "password"---but "admin" proved most popular.
Another password used in many hacking attempts was "vivx," which is a default for DVRs made by Chinese company Dahua. Two other passwords on the list--- "1001chin" and "taZz@23495859"---are also factory defaults for other embedded devices, including routers.
It's revealed that 99.9 percent of traffic to the honeypots came from bots, malware, and other tools. These attacks can come from any connected device, from traditional PCs to smartwatches and even IoT toothbrushes.
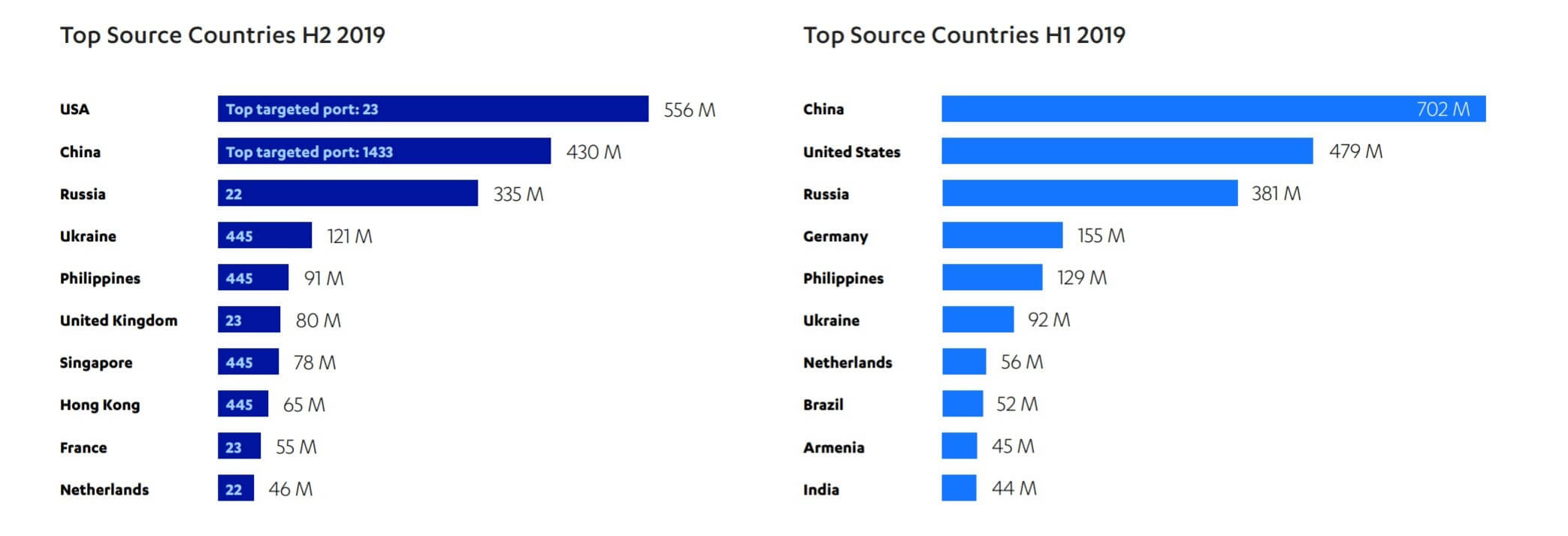
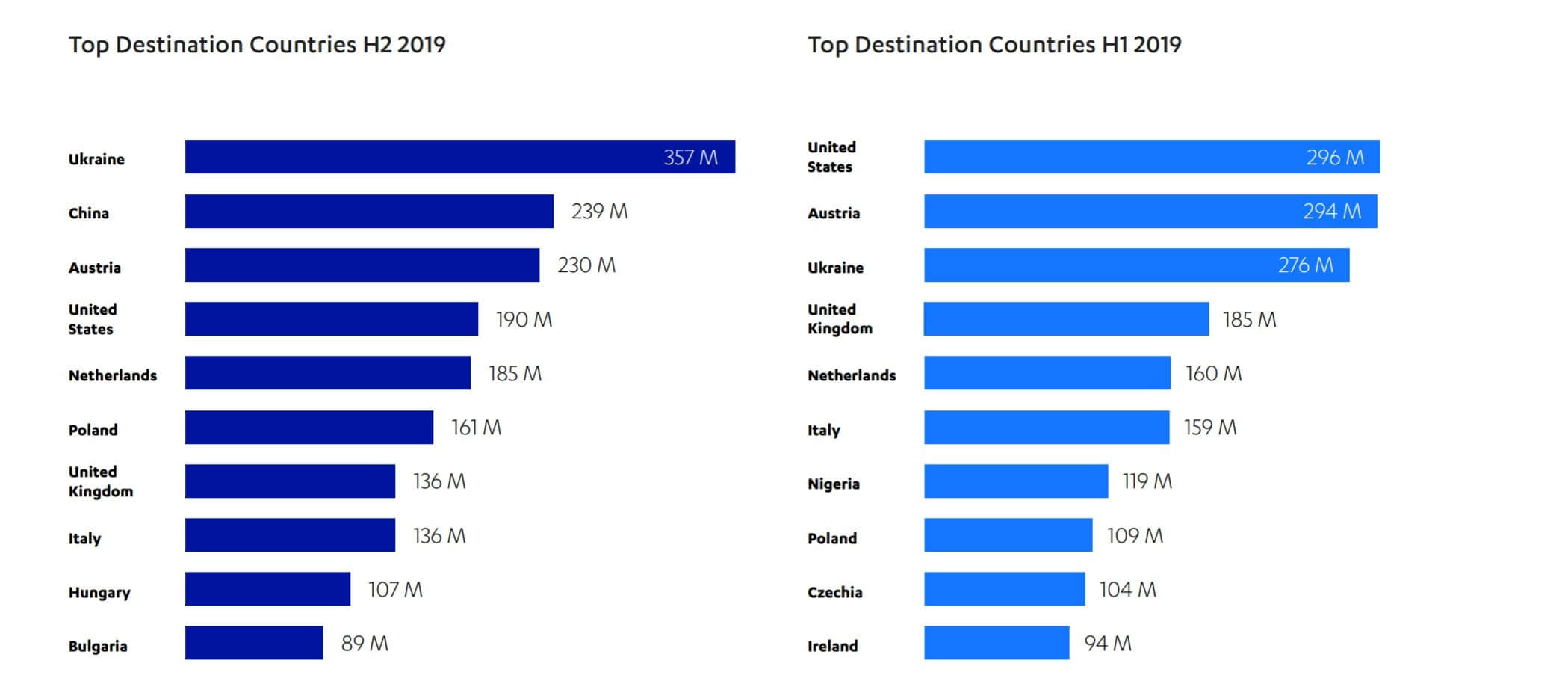
Most of the attacks came from the US, followed by China and Russia. It's noted, however, that many attackers route their attacks through proxies in other countries to avoid identification, so the list should be taken with a grain of salt. As for the top attack destinations, Ukraine was number one, followed by China, Austria, and the US.
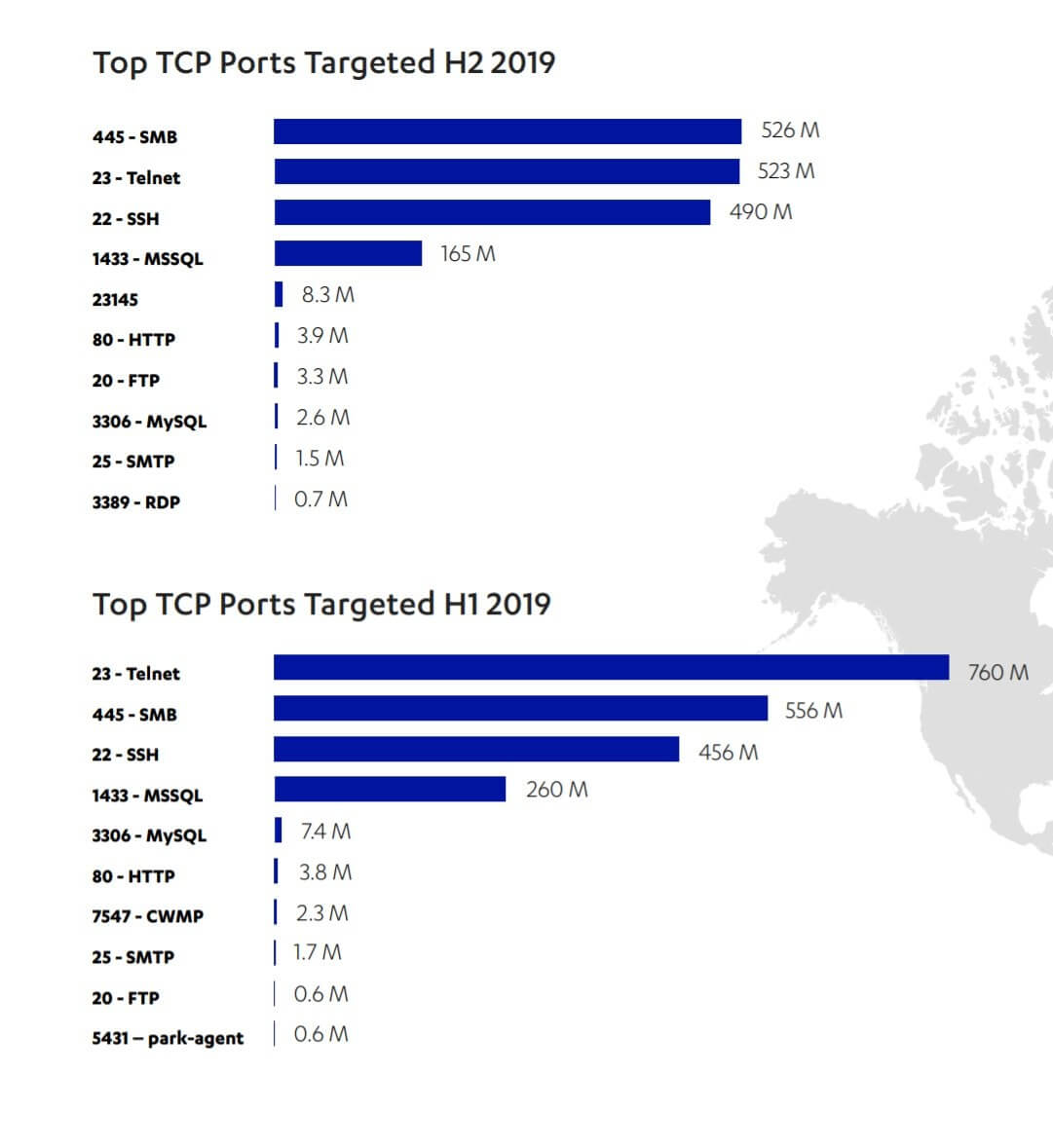
When it comes to the top TCP ports targeted, SMB Port 445 was most popular with 526 million hits, showing that attackers are still keen to use SMB worms and exploits such as Eternal Blue, like Trickbot. Telnet was second with 523 million hits, indicating that attacks on IoT devices remain common.
The report is another reminder for consumers to change their devices' default passwords and factory settings, and to follow standard safety precautions such as keeping up to date with the latest firmware updates and patches. Also, don't use terrible passwords.
Image credit: Vitalii Vodolazskyi via Shutterstock