In brief: Huawei is mostly known for its mobile products and telecom equipment, but its HiSilicon subsidiary produces chips that end up in many IoT products, including surveillance systems. A Russian researcher found that most of the companies that use HiSilicon chips use firmware that makes it trivial to take complete control of millions of devices that are currently in use around the world.
Back in December, Huawei said it had reached record revenues of $122 billion, even as the US greatly restricted its ability to do business with American companies. Between the optimistic lines in its report, the Chinese giant warned that 2020 would be a challenging year, with lots of bumps in the road.
However, the company probably didn't expect to see yet another security vulnerability affecting one of its products be disclosed just as it's tackling coronavirus concerns.
Recently, Russian security researcher Vladislav Yarmak published a worrying analysis of backdoor mechanism discovered in Hangzhou Xiongmai Technology firmware, which makes it trivial to take control of millions of security cameras, DVRs, NVRs, and other IoT devices using HiSilicon chips.
For those of you who don't know, HiSilicon is a Huawei subsidiary that makes the chips that go in all of its products, including the fancy foldable Mate X smartphone that costs $2,400 and is reportedly selling better than Samsung's Galaxy Fold. To put things in context, HiSilicon is the largest of the Chinese silicon giants, with many companies relying on its integrated circuits for their various products.

Yarmak says the backdoor mechanism is actually using a mix of exploits that take advantage of bugs that were discovered years ago, in 2017 and even as far back as March 2013. And since reporting those previous vulnerabilities led to no actual fix being deployed by HiSilicon, the researcher recommends owners of devices using HiSilicon chips switch as soon as possible to alternative solutions.
You can find a list of known brands affected here. If you can't afford the hardware switch, Yarmak noted you should bolster security by restricting access to device ports 9530/TCP, 9527/TCP, and 23/TCP - all of which can be exploited using the proof of concept code he published on GitHub.
The way it works is that some older versions of the firmware used in products that are based on HiSilicon SoCs rely on access to telnet for remote connections. Telnet is enabled by default on these, so an attacker can get full access to these devices by using "a static root password which can be recovered from the firmware image with relatively little computation effort."
Newer versions of the firmware come with telnet access disabled by default, but also have TCP port 9530 open for special commands, a feature which Yarmak says was intentionally baked in by HiSilicon, who didn't bother to fix the new exploit published for it in 2017. Add to that the questionable practice of keeping a short list of static passwords that act as a backdoor to millions of IoT and surveillance products used worldwide, and you have a security nightmare.
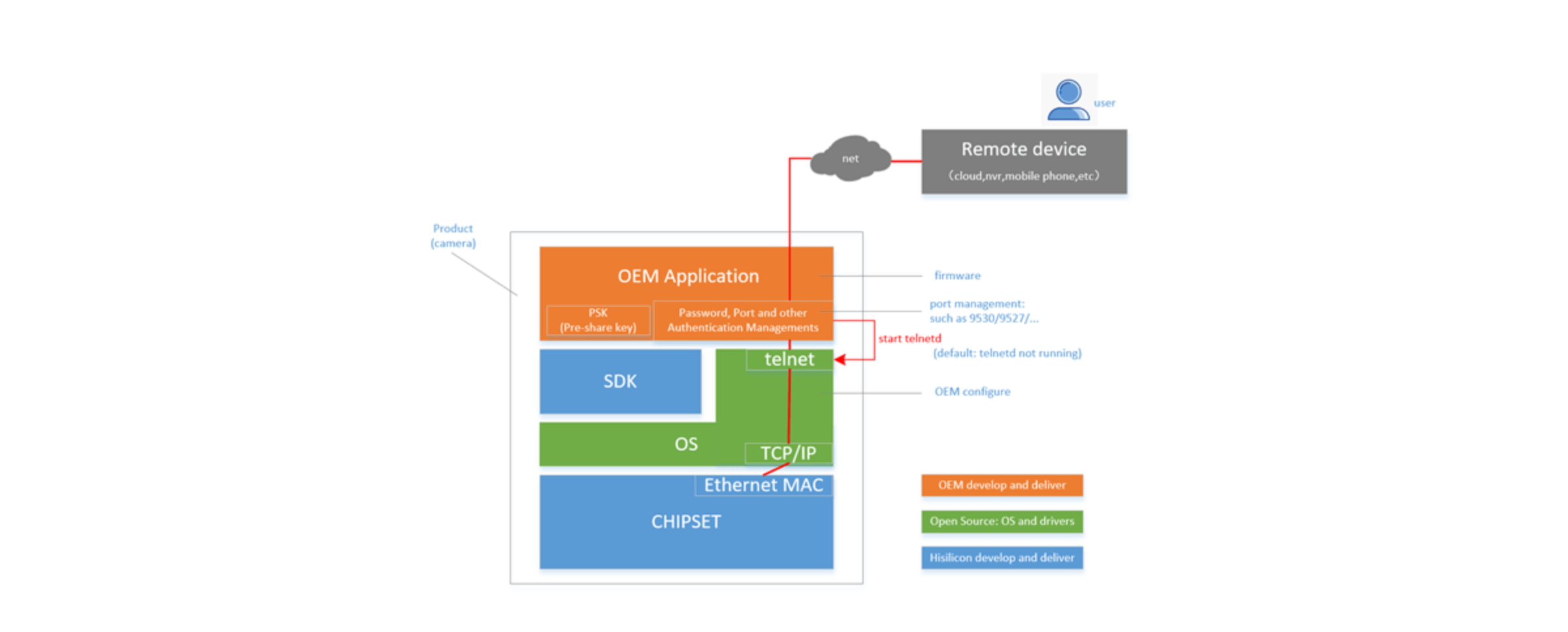
To be fair, HiSilicon isn't directly responsible here, as the vulnerability only affects products that use firmware developed by Xiongmai Technology and XMtech. The Huawei subsidiary published a security notice explaining that its SDKs don't have the vulnerability presented by Yarmak in his report. The company noted that "Huawei (and its affiliates worldwide, including HiSilicon) has long committed that it has not and will never place backdoors nor allow anyone else to do so."
As far as Huawei is concerned, the Telnet services were deleted on all devices it distributes directly to end users. Also, the overall narrative hasn't changed - last year, the Chinese giant insisted that backdoors found by Vodafone in critical network equipment were "weaknesses." To this day, the company is still fighting for the right to supply equipment to rural carriers in the US, even though its chances remain low.