The big picture: China has been using BGP hijacking to re-route western internet traffic through one of its biggest telecoms. The attacks have been occurring at least since it entered into an agreement with the US to halt state-sponsored cyber theft. Ten points-of-presence have been tracked down in the US and Canada, which are being maliciously used by the Chinese government.
According to a paper by the US Naval War College and Tel Aviv University, China has been hijacking the internet backbone of western countries since 2015. The study was published in the academic journal Military Cyber Affairs.
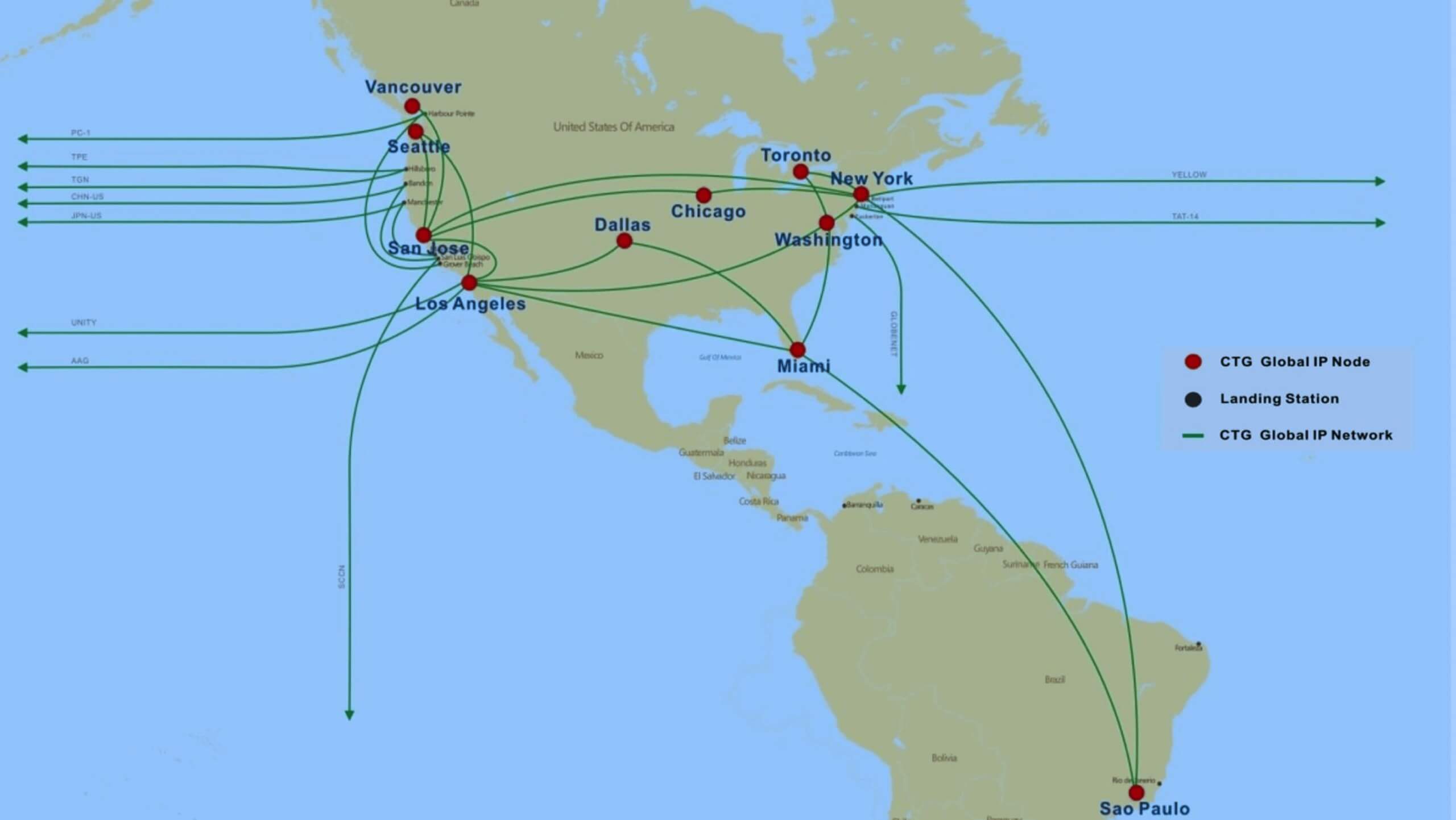
It asserts that China Telecom, one of the country's leading internet service providers and phone companies has been using points-of-presence (PoP) to perform man-in-the-middle interceptions. CNET explains that a PoP is merely a data center that re-routes traffic between the smaller networks that make up the internet.
Internet traffic travels through these autonomous systems (AS) using the Border Gateway Protocol (BGP). Unfortunately, the BGP has no real security features, and it is not challenging to intercept data by announcing a malicious route. This is called a BGP hijack, and it occurs frequently. However, in most instances, the hijack is due to a misconfiguration rather than malicious intent and is therefore corrected within minutes or hours.
According to the researchers, the communist state has been using China Telecom purposefully to conduct BGP hijacking. It started doing this in 2015 in earnest shortly after signing an agreement under the Obama administration that was intended to halt the government-backed cyber theft of intellectual property.
"This necessitated new ways to get information while still technically adhering to the agreement," the researchers wrote. "Since the agreement only covered military activities, Chinese corporate state champions could be tasked with taking up the slack. Enter China Telecom."
The study has tracked the BGP abuse by building a system that traces and monitors BGP announcements. Using this system, they can identify patterns that suggest deliberate hijacking.
They have been able to track down a total of ten PoPs being used to carry out the attacks --- eight in the United States and two in Canada. These points-of-presence have been covertly built over the course of several years beginning in the early 2000s.
"Using these numerous PoPs, [China Telecom] has already relatively seamlessly hijacked the domestic US and cross-US traffic and redirected it to China over days, weeks, and months," the study found. "While one may argue such attacks can always be explained by 'normal' BGP behavior, these, in particular, suggest malicious intent, precisely because of their unusual transit characteristics -namely the lengthened routes and the abnormal durations."
The researchers call for immediate action to be taken to take the rogue nodes down.
"The prevalence of and demonstrated ease with which one can simply redirect and copy data by controlling key transit nodes buried in a nation's infrastructure requires an urgent policy response."
Image via Military Cyber Affairs
