Hackers have exploited an eight-month-old flaw in Asus routers, giving anyone access to data stored on drives connected directly through the USB port on the back. Some affected users have found text files on their connected drives informing them they've been hacked, with instructions on how to protect themselves.
"This is an automated message being sent out to everyone effected [sic]. Your Asus router (and your documents) can be accessed by anyone in the world with an Internet connection," the message reads. Finding this message on their connected drive has alarmed some users, who believed that the drive was only accessible through their local network.
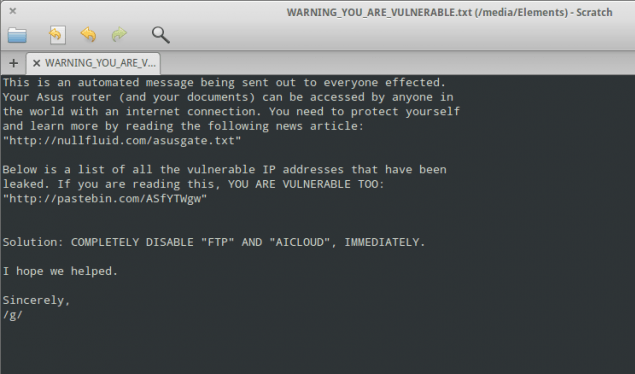
This particular router vulnerability was publicly uncovered by researcher Kyle Lovett back in June of 2013, after Asus insisted the behavior "was not an issue". In July, Lovett published technical details on how the drives can be accessed, which presumably was used by a hacker group to access data from many Asus router owners worldwide.
The hacker group in question posted nearly 13,000 IP addresses of people with vulnerable Asus routers two weeks ago, along with a torrent containing 10,000 complete or partial file lists detailing data on connected drives.
Affected Asus router models include the RT-AC66R, RT-AC66U, RT-N66R, RT-N66U, RT-AC56U, RT-N56R, RT-N56U, RT-N14U, RT-N16, and RT-N16R. Luckily, firmware updates for the routers that patch the exploit have been available since last week, however many potentially vulnerable users are yet to install the patch.
If you do have an Asus router, we strongly recommend you install the latest firmware updates, change the router's default password, and disable cloud and FTP options that could allow external access to your drives.