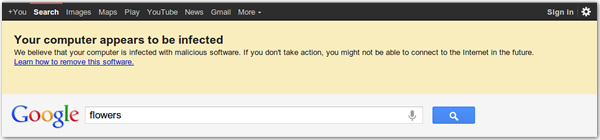
Google has begun providing a warning to visitors who appear to be infected with DNSChanger, a malware which attempts to redirect users to various websites by modifying their DNS settings. The notification is a highly visible alert which tells the user they are infected and links to instructions for removing DNSChanger.
In February, we reported that over 4 million computers were infected with the bug.
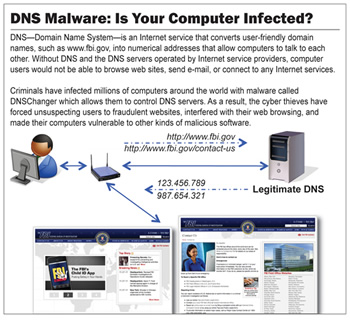
Google's initiative is spurred by the expiration of a court order on July 9. Once the court order ends, there will be no obligation for the Internet Systems Consortium to maintain temporary DNS servers which allow users infected with DNSChanger to remain online. With the shutdown of DNSChanger's infrastructure and the discontinuation of those temporary servers, infected users will have invalid DNS settings – a problem which effectively results in no Internet access. To understand this though, you need to also understand a little bit about how DNS and DNSChanger works.
In really basic terms, DNS, or "domain name system" is an important service through which Internet domains (e.g. techspot.com) point web surfers to the correct websites and servers. Without DNS, the Internet would be a very unfriendly place.
When a computer is infected with DNSChanger, the malware modifies the PC in such a way that it bypasses bona fide DNS servers. Legitimate DNS settings are often provided by your ISP automatically, but can also be set manually – and wrongly, at that. DNSChanger would then redirect that user's Internet traffic through its own DNS servers. From then on, as an infected user cruises the web, the malware's rogue servers would deceptively redirect that person to advertisements, illicit or dangerous material and spy on them without their knowledge.
Particularly dangerous was DNSChanger's ability to also change DNS settings on routers, effectively spreading the issue from a local computer to an entire network. For some users, even after their computers are malware-free, issues will persist until they remove the harmful changes made to their router.
It is interesting to note that Google performed a similar service last summer, in order to protect its users from an unrelated DNS-based malware attack.
Users can check if they are infected with DNSChanger here and may remove the malware by following these instructions.