In context: Kaspersky said the attack managed to fly under the radar for so long due to the fact that the trojanized updater was signed using legitimate certificates from Asus. As such, nobody ever suspected anything was amiss.
Hackers in 2018 reportedly compromised a server hosting Asus' Live Update tool and used it to distribute a malicious backdoor to unsuspecting Windows machines.
Kaspersky Lab on Monday said it discovered the sophisticated supply chain attack on Asus' Live Update Utility in January and promptly informed the company. According to its investigation, the attack took place between June and November 2018.
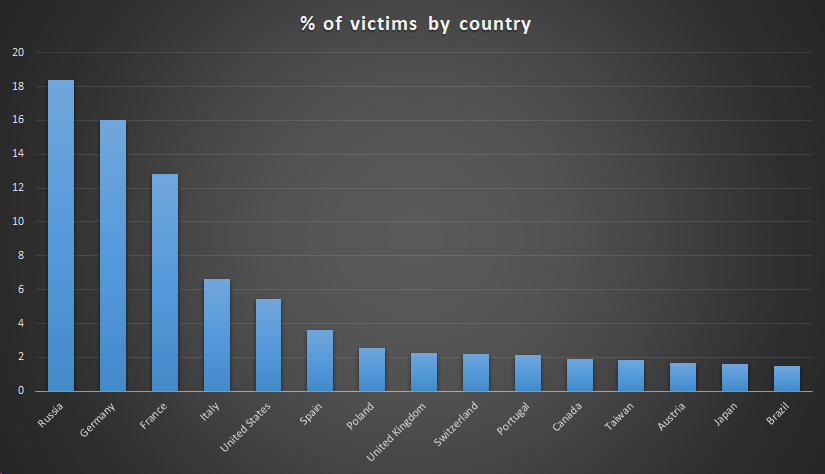
Kaspersky said over 57,000 of its users have downloaded and installed the backdoored version of Asus Live Update but the issue may possibly affect over a million users worldwide.
The security company classified it as a highly sophisticated attack that matches or may even surpass recent ShadowPad and CCleaner incidents in complexity and technique. The goal of the attack, Kaspersky said, "was to surgically target an unknown pool of users, which were identified by their network adapters' MAC addresses." They're calling this new attack Operation ShadowHammer.
Kaspersky has linked the attack to the ShadowPad incident from 2017. Microsoft has previously identified the actor behind that incident to be known as "Barium."
Kaspersky created a tool that can determine if your computer was specifically targeted in the attack by comparing MAC addresses.
Kaspersky Lab plans to share a full technical paper on the matter as part of a presentation at the Security Analyst Summit in Singapore next month.
Lead image courtesy BeeBright via Shutterstock
