Why it matters: Password managers may be flawed but the benefits seemingly outweigh the shortcomings. Aside from assisting in categorizing credentials, they help users avoid bad password practices such as password reuse and weak password selection.
As security researcher Troy Hunt once wrote, "Password managers don't have to be perfect, they just have to be better than not having one." According to a recently published report from Independent Security Evaluators (ISE), they've more or less accomplished that goal.
ISE put five popular password managers to the test - 1Password4 for Windows version 4.6.2.626, 1Password7 for Windows version 7.2.576, Dashlane for Windows version 6.1843.0, KeePass Password Safe version 2.40 and LastPass for Applications version 4.1.59 - to see just how secure they are.
The researchers found that in every case, trivial secret extraction was possible from a locked password manager. In some cases, they were even able to collect the master password.
With 1Password4, ISE found reasonable protections against exposure of individual passwords in the unlocked state. However, it is possible to recover and deobfuscate the master password due to the fact that it isn't scrubbed from memory after placing the manager in a locked state.
Surprisingly enough, ISE said the current release, 1Password7, was less secure in the running state than the aforementioned legacy version. Unlike 1Password4 which kept only one entry at a time in memory, 1Password7 decrypted all individual passwords as soon as it was unlocked and cached them in memory. Worse yet, the manager doesn't scrub individual passwords, the master password or the secret key from memory when transitioning from unlocked to locked state.
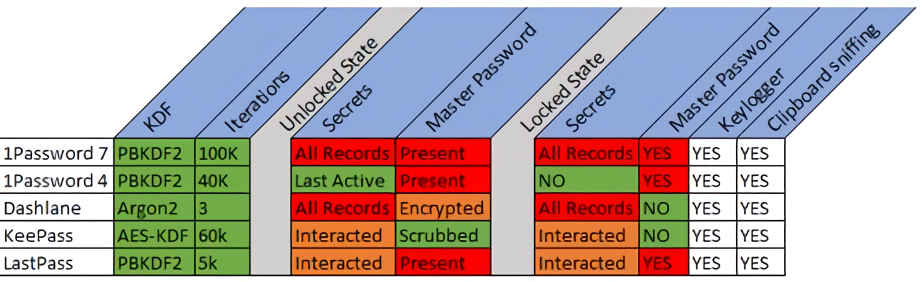
In testing Dashlane, ISE noted the use of memory / string and GUI management frameworks to prevent secrets from being passed to various OS APIs that could expose them to eavesdropping by malware. Dashlane also only exposes one active entry in memory at a time although unfortunately, "once a user updates any information in an entry, Dashlane exposes the entire database plaintext in memory and it remains there even after Dashlane is logged out of or 'locked'."
Like 1Password4, open-source KeePass decrypts entries as they are interacted with but critically, they all remain in memory as they aren't individually scrubbed after said interaction. On the bright side, ISE found that the master password is scrubbed from memory and thus, not recoverable.
LastPass is similar to 1Password4 in that it obfuscates the master password as it is being typed into the unlock field. Once the manager enters an unlocked state, database entries are decrypted into memory although only upon user interaction. Unfortunately, the entries linger in memory even after LastPass is put back into a locked state.
In conclusion, ISE notes that all password managers tested sufficiently secured secrets while in a "not running" state, meaning if someone gathered a database from a disk and if a strong master password was used, brute forcing would be computationally prohibitive. However, each also fails in implementing proper secrets sanitation for various reasons.
Lead image courtesy EtiAmmos via Shutterstock
