Cybersecurity: Most tech enthusiasts have probably heard of white-hat hackers. In short, it is a term used to describe those who use their affinity with hacking for good. They dig into software and website code to discover and disclose potential exploits to the public, or those who maintain said software.
Most large companies recognize the value these hackers offer to the tech industry, and have set up lucrative "bug bounty" programs to reward them for their efforts depending on the severity of any disclosed bugs.
Traditionally, the process of bug-hunting is something that is mostly handled by human beings. After all, nothing can beat a real person's attention to detail - right? Not quite, according to a new report from IEEE Spectrum.
Written by security researcher David Brumley, the report describes the rise of what might be one of the worlds' most impressive automated white-hat hacking machines. Called Mayhem, the machine is a water-cooled computing behemoth that can detect, exploit, and fix software weaknesses automatically, and at speeds that no human being can match.
So, how does Mayhem work? The gist is that it combines two long-standing approaches to software analysis to perform its duties, known as "fuzzing" and "symbolic execution."
In the words of Brumley himself:
Symbolic execution builds an equation to represent all the logic in a program---for example, "x + 5 = 7"---and then solve the equation. Contrast this strategy with another method of software analysis known as fuzzing, in which you feed random permutations of data into a program to crash it, after which you can determine the vulnerabilities that were at fault and how they might be exploited in a more deliberate attack. Fuzzing keeps putting in random data until a particular string of data makes the equation true, finally determining that x =2.
Put into even simpler terms, fuzzing involves "making intelligent guesses at lightning speed," and symbolic execution is like "asking a mathematician to try to formally figure out what inputs may exploit [a] program."
During internal tests, Mayhem managed to find a whopping 14,000 unique vulnerabilities when set loose on every program in popular Linux distribution Debian; 250 of which were completely new.
Mayhem's team of creators, which is comprised of Brumley and several researchers from Carnegie Mellon University, decided to enter the device into a hacking contest led by DARPA back in 2015. Throughout the competition, contestants' machines earned points based on how many vulnerabilities they managed to find, exploit, and patch.

The contest was split into two phases: a qualifying round, and a finalist event known as the Cyber Grand Challenge (CGC).
ForAllSecure's (the name of Brumley's team) Mayhem managed to score twice as many points as the next best-ranked semifinalist in the qualifying round, and at the CGC itself, the machine once again prevailed against its six competitors - but it wasn't the victory itself that was impressive.
Rather, it was how Mayhem won that astonished spectators. A mere 40 rounds into the CGC, Mayhem crashed, devastating the ForAllSecure team. However, at the end of the contest, it was revealed that their sadness was for nought - Mayhem still managed to win, despite not being functional for the remaining 55 rounds of the CGC.
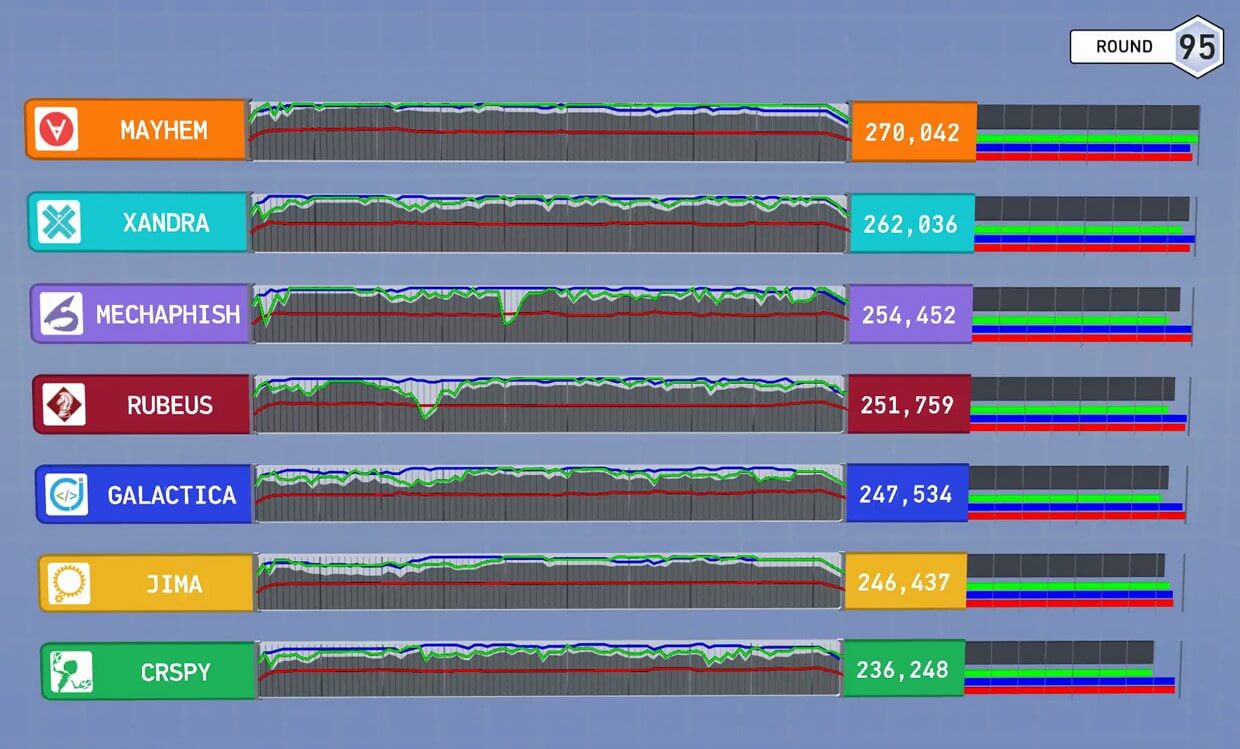
Though we'll never know how far Mayhem could have gone if it hadn't crashed, it is probably safe to say the machine would have far surpassed the scores of its competitors.
According to Brumley, the machine's capabilities are currently being sold to "early adopters" such as the US government, as well as various tech and aerospace companies.
However, given the risks associated with giving Mayhem free reign over such important industries, the machine is still working alongside human security experts - for now. In the future, Brumley believes machines alone will handle the world's cybersecurity.
Image courtesy DARPA, Sean McCabe, & Chelsea Mastilak via IEEE Spectrum
