Why it matters: Unknown attackers developed a way to use memes posted to Twitter to control RAT-infected computers. The operators use steganography to hide the instructions in images, which the malware then parses and executes. The hackers can retrieve data such as usernames, directories, clipboard contents, running programs, and screenshots. The malicious individuals have not been identified.
Security researchers at Trend Micro have discovered a new type of malware that retrieves its instructions from memes posted to Twitter. The malware itself is a relatively rudimentary remote access trojan (RAT).
Once infected the program can take screenshots or pull data from the computer and relay it to a central server controlled by the hacker. What makes this particular RAT (detected as TROJAN.MSIL.BERBOMTHUM.AA) unique is the use of steganography to give it commands.
Steganography is a technique that hides code within memes. The malware downloads the images from a Twitter account that was created in 2017. It then parses the embedded data into commands that it executes.
Trend Micro only found two tweets on October 25 and 26 that delivered "/print" commands to the malware, which told it to take screenshots on the infected computer. The malware then sends the images to a command and control server. The server's address obtained by the malware through a "hard-coded" URL on Pastebin.
It would seem that because of the limited number tweets found on the malicious account, the malware may have just been in the early stages of development. The hackers may have created it just as a proof of concept with plans to develop something more sophisticated later.
There are a variety of other commands that the malware operators could have used. To get a list of running apps, for example, "/processos" could have been used. To grab a dump of the user's clipboard, operators simply use "/clip." Retrieving filenames from specific folders requires the "/docs" prompt and "/username" returns the username on the device.
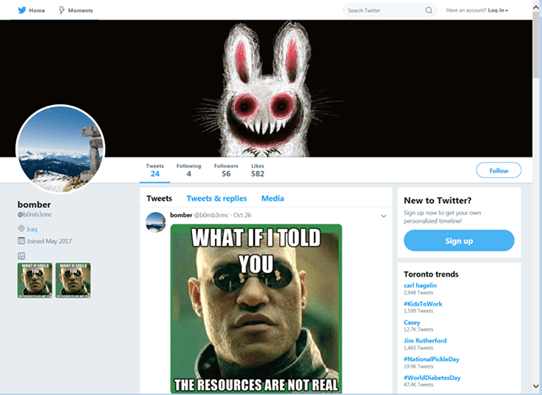
The Twitter account used has the handle of "bomber." Researchers mentioned that Twitter is not the delivery method for the trojan itself, just the commands. The account appears to have been taken down now.
Trend Micro is unsure what vector is used to infect machines. Researchers will undoubtedly study the malware in depth and apply what they learns to create countermeasures for the company's "Smart Protection Suites."