In brief: Researchers at the University of California at Riverside have discovered three ways that hackers can use graphics processing units to compromise users' security and privacy. The techniques can be used to spy on browser activity, steal passwords, and to attack cloud-based applications.
In a paper titled "Rendered Insecure: GPU Side Channel Attacks are Practical," the computer scientists describe how they were able to reverse engineer an Nvidia GPU to compromise both graphics and computational stacks. They contend that this is the first time anyone has successfully used side channel attacks on a GPU.
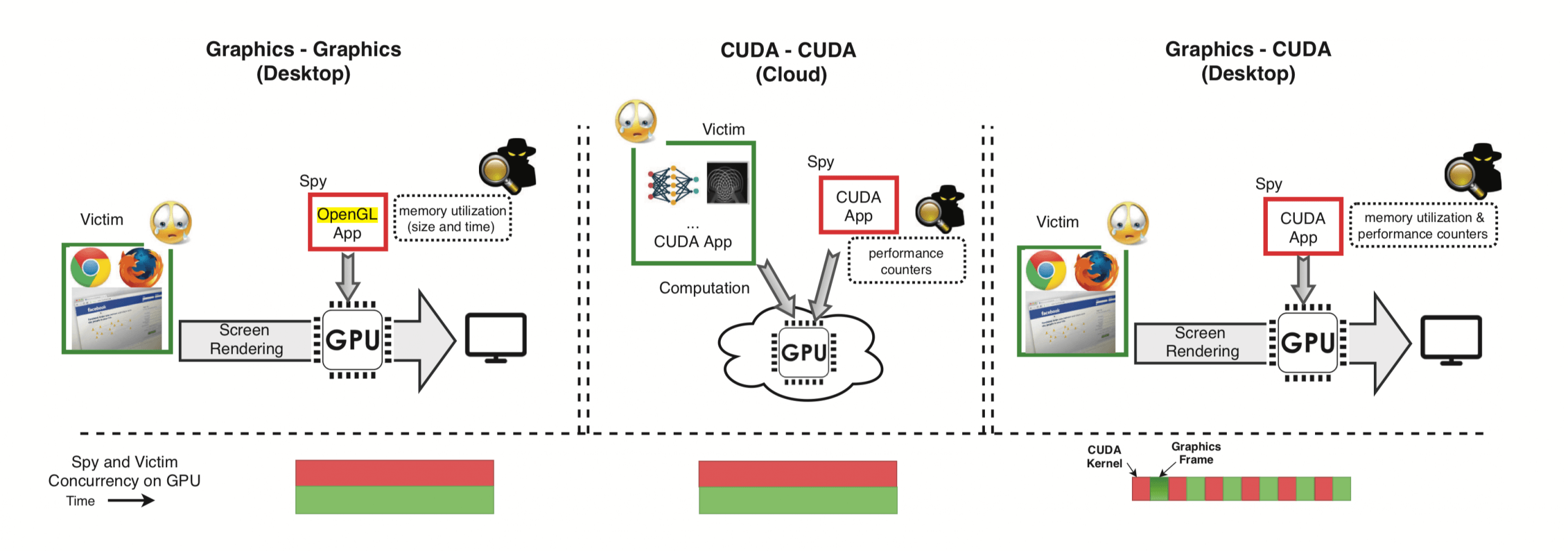
There are a couple of requirements to execute these types of exploits. First, the victim must install a spyware program. This malicious code could be embedded in an otherwise innocuous application. Second, the attackers must have a machine-learning algorithm that can analyze memory allocations of the GPU. Both the spyware and the ML program utilize existing graphics APIs such as OpenGL or WebGL to execute the attacks.
Once the user opens the malicious application, it uses the APIs to analyze the browser as it is being rendered by the GPU. Memory allocations and performance counters from the GPU are monitored and fed into the machine-learning algorithm, which interprets the data to create a fingerprint of the website.
"Every website has a unique trace in terms of GPU memory utilization due to the different number of objects and different sizes of objects being rendered," notes UC Riverside. "This signal is consistent across loading the same website several times and is unaffected by caching."
According to the researchers, they have been able to achieve very high accuracy using this website fingerprinting method. This technique could allow hackers to monitor all web activity.
The team was also able to extract passwords from the GPU data. As a user types in their password, the entire text box is sent to the graphics processing unit for rendering. This passing of data occurs for each keystroke.
"Monitoring the interval time of consecutive memory allocation events leaked the number of password characters and inter-keystroke timing, well-established techniques for learning passwords," they said.
The third technique is used to attack cloud-based applications. It is a bit more complicated than the other methods.
"The attack targets a computational application in the cloud. The attacker launches a malicious computational workload on the GPU which operates alongside the victim's application. Depending on neural network parameters, the intensity and pattern of contention on the cache, memory and functional units differ over time, creating measurable leakage. The attacker uses machine learning-based classification on performance counter traces to extract the victim's secret neural network structure, such as number of neurons in a specific layer of a deep neural network."
The team already informed Nvidia of their findings and were told that the company would be rolling out a patch to system administrators that would give them the option to disable access to performance counters from user-level processes. They also communicated their research to AMD and Intel security teams so that they could assess whether these vulnerabilities could be exploited on their respective GPUs.
If you are interested, the researchers have uploaded their paper to the UCR website. The group now plans to test against Android phones to see if GPU side-channel attacks are possible.
