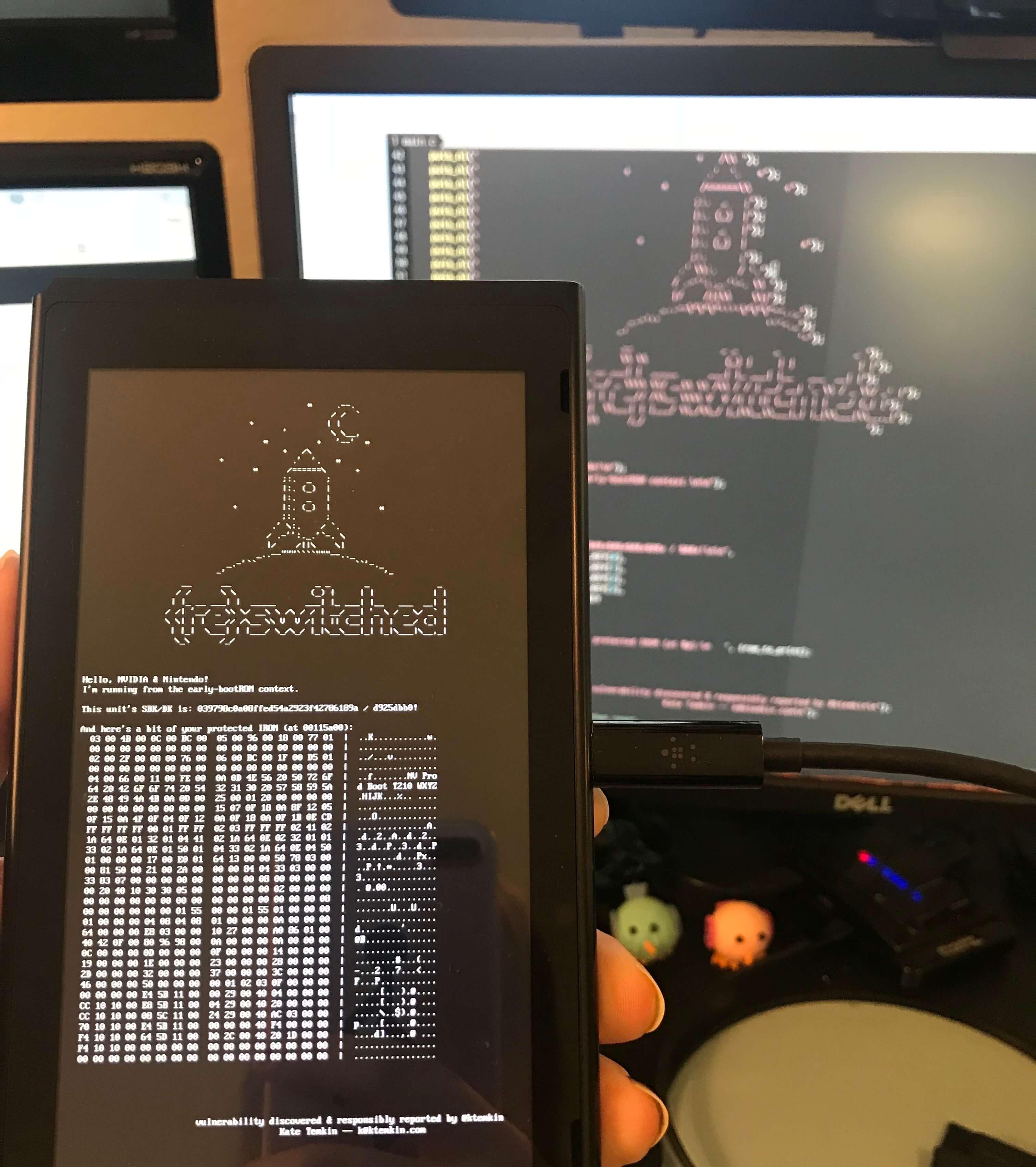
Due to a recently published exploit for Nvidia's Tegra X1, developers and hardware hackers at ReSwitched and Fail0verflow have been able to demonstrate arbitrary code execution on the Nintendo Switch. The Fusée Gelée (or rather Frozen Rocket) coldboot vulnerability allows for nearly full reign over the device by inserting data into the protected application stack.
The issue stems from a problem with how the Tegra X1 handles USB recovery mode. By shorting a pin on the Joy-Con connnector, a payload is able to be delivered during a check made to the USB, forcing up to 65,535 bytes to be copied. This in turn causes a direct memory access buffer overflow in the bootROM, allowing for arbitrary code execution to occur in the application stack.
Since the problem lies in the read-only bootROM of the Tegra, software updates cannot be pushed out to remedy the problem. It is possible for Nvidia to revise future software versions and ship patched chips from this point forward.

The ReSwitched team has reported that Nvidia was made aware of the vulnerabilities as well as Nintendo in advance before releasing any information. It was also brought to light that many devices beyond Switch consoles are affected by the bugs found. Nvidia's Shield set-top box also utilizes the same Tegra X1 chip.
Following the release of the exploit chain, it will be possible for pirates and hackers to run modified and emulated games on the Switch. It is now only a matter of time before developers rush to crack DRM on games. Even though Nintendo cannot fix the root of the issue, it is possible to detect that a Switch has been modified so that players can be blocked from accessing online game play.
If anyone is curious to try tinkering for themselves, it is highly inadvisable without extreme caution given that voltages on the Switch are software controlled. A failed boot attempt could brick the device or damage a number of components.