It would seem that your brand-spanking new Android phone is not as secure as you think it might be. According to a two-year study conducted by Security Research Labs (SRL) on more than 1,200 Android phones, many are missing security patches. Even worse is the fact that the manufacturers of these handsets are lying when they say that their firmware is fully updated.
SRL researchers Karsten Nohl and Jakob Lell back engineered phones from Google, Samsung, HTC, Motorola, ZTE, TCL, and others checking at the source-code level to see if all the patches were present. What they discovered was something they refer to as "patch gap."
These are places in the code where updates should be but are not. While the phone's software may claim to be fully up-to-date, the researchers found security patches missing in most devices. On some phones, the patch gaps numbered in the dozens.
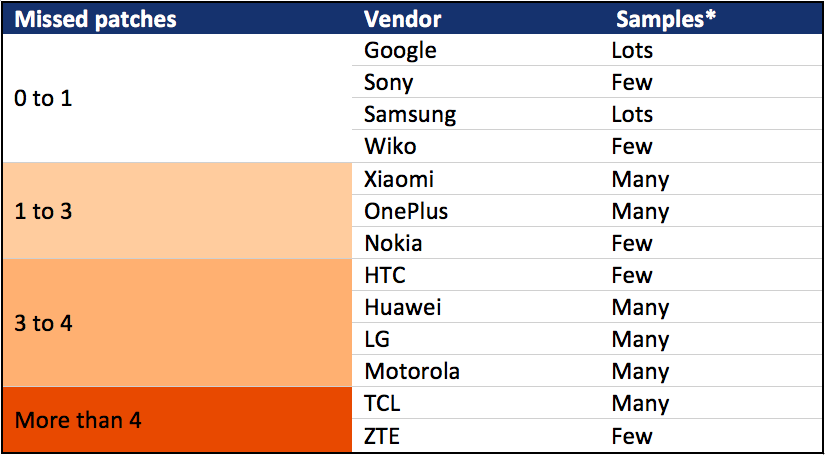
Some manufacturers fared better than others. Sony and Samsung devices were found to have only skipped 0-1 security update. Xiaomi, OnePlus, Nokia jumped as many as three patches. Huawei, HTC, Motorola, and LG were found to be lacking up to four, and ZTE and TCL were missing more than four updates in many cases. Not surprisingly, all Google phones were found to have every patch released present.
The researchers did find a correlation between skipped patches and chipsets, however. According to the study, phones with Samsung-made chips had much fewer skipped updates. MediaTek chipsets, on the contrary, had an average of 9.7 missing security patches.
"You should never make it any easier for the attacker by leaving open bugs that in your view don't constitute a risk by themselves, but may be one of the pieces of someone else's puzzle."
Google told Wired, "some of the devices SRL analyzed may not have been Android certified devices, meaning they're not held to Google's standards of security."
Scott Roberts, Android's product security lead also noted that security patches are only one level of protection built into Android devices.
"Built-in platform protections, such as application sandboxing, and security services, such as Google Play Protect, are just as important," he said. "These layers of security---combined with the tremendous diversity of the Android ecosystem---contribute to the researchers' conclusions that remote exploitation of Android devices remains challenging."
The takeaway here is that even though a new phone might not have every single patch, the Android OS is still tough to hack. The researchers agree with this assertion. However, does this excuse manufacturers who say their devices are fully updated when they are not?
As Nohl puts it, "You should never make it any easier for the attacker by leaving open bugs that in your view don't constitute a risk by themselves, but may be one of the pieces of someone else's puzzle. Defense in depth means install all the patches."