Nobody wants to become the victim of hackers who compromise online accounts, yet it's something that 15 percent of internet users have reported experiencing. Following a year-long study by Google and UC Berkeley, we know that data breaches are the most popular method of stealing users' credentials, but phishing scams are more dangerous because of the extra information that's exposed.
From March 2016 to March 2017, Google and UCB trawled public and private hacker forums and paste sites to search for stolen log-in names, passwords, and other account details. Google said the investigation showed how this information was obtained.
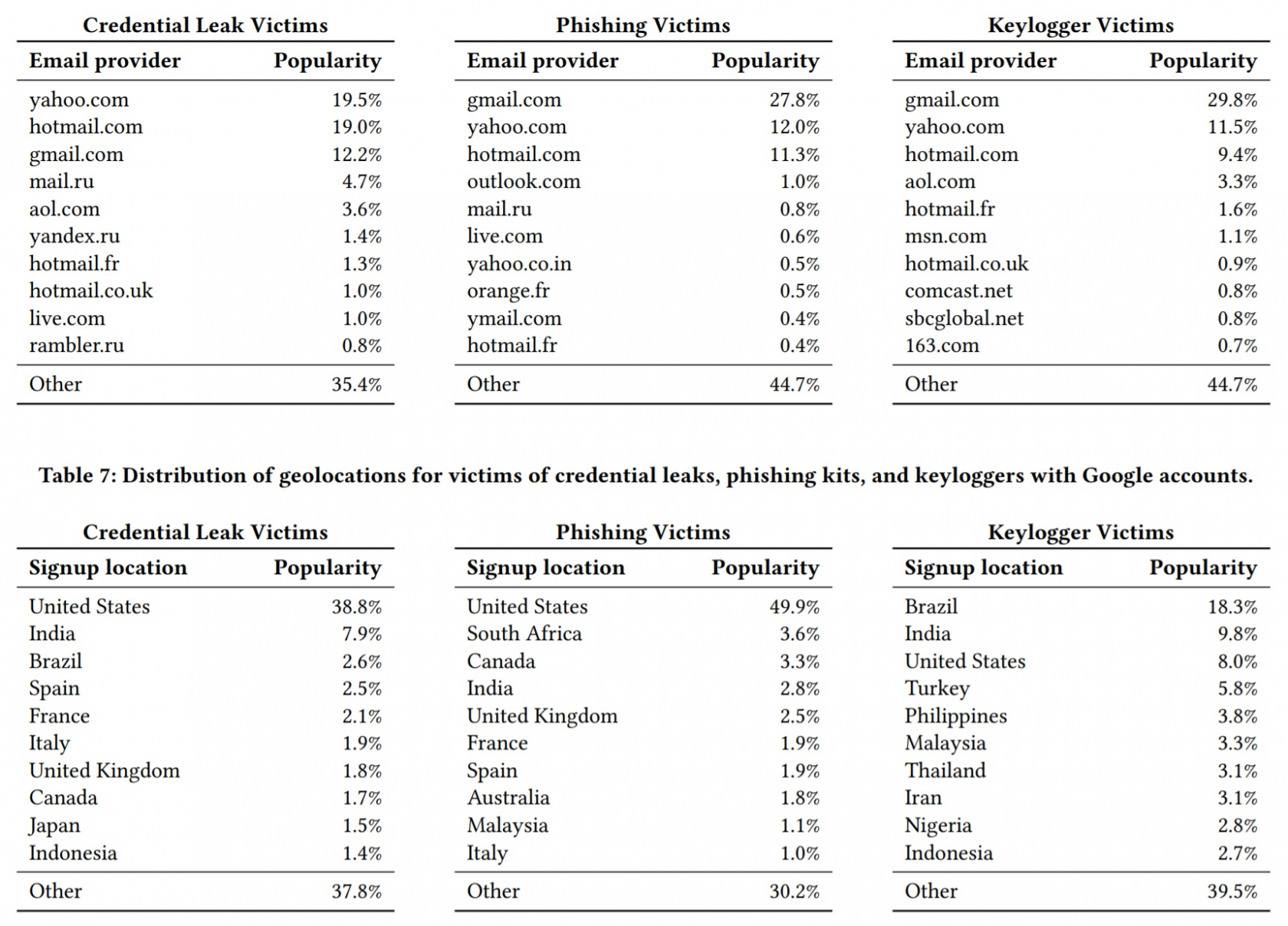
It turns out that data breaches are the most common way for user credentials to leak online, which isn't that surprising, given their regularity and size. Prominent breaches such as those by Yahoo, LinkedIn, and MySpace contributed to 1.9 billion records being leaked, most which were being traded on private forums. 12 million credentials were obtained though phishing kits, while 780,000 credentials came from keyloggers.
12 percent of the records exposed through data breaches used Gmail addresses, and 7 percent of these cases saw the same password used for both accounts. The success rate is higher when using phishing and keyloggers: 12 - 25 percent of passwords obtained using these attacks yielded valid passwords. Around 234,000 valid names and passwords are obtained through phishing every week, whereas keyloggers yielded about 15,000 valid credentials each week.
In terms of risk to the user, phishing was the greatest threat, followed by key loggers then third-party breaches. While the victim of a data breach is ten times more likely to have their account taken over than a random Goole user, someone who falls for a phishing scam is 400 times more at risk. This is because of the way phishing kits obtain information such as secret questions, device identifiers, geolocations, IP addressed, and phone numbers.
Over 4000 distinct phishing kits were discovered during the study, the most popular of which emulates Gmail, Yahoo, and Hotmail login pages. Most of the kits originate from African and East-Asian countries, with Nigeria having the highest concentration of operators.
While it's not infallible, two-factor authentication remains the best way to protect your online accounts. If you want even more protection, there's U2F USB security key support for accounts such as Facebook, Google, and Dropbox.
