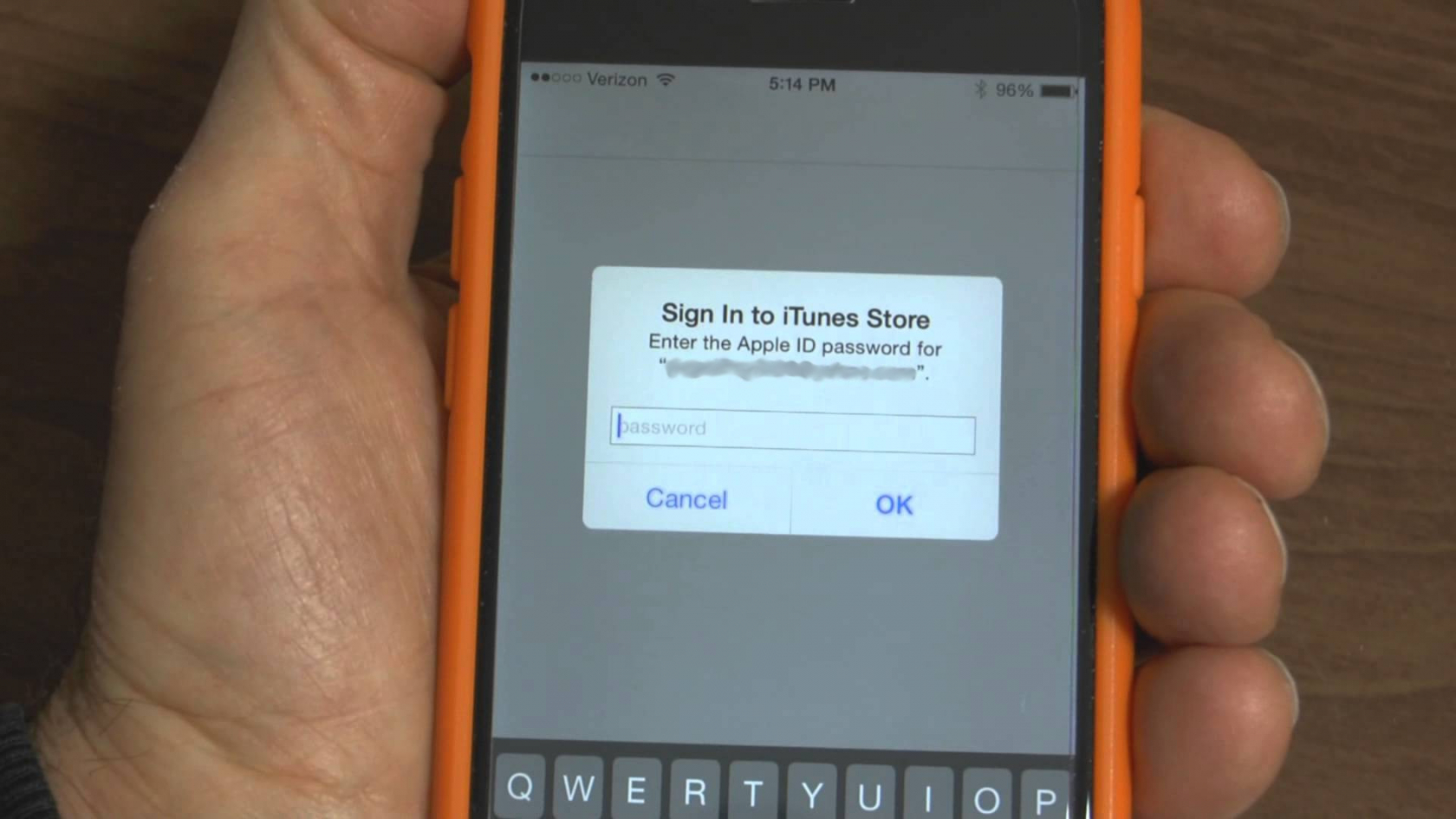
For all its bells and whistles, iOS is a relatively reliable and secure platform. After all, not even the FBI could crack Syed Rizwan Farook's iPhone 5C without help and has since admitted that the technique used will not work on newer iPhones.
However, iOS does have one vulnerability that has flown under the radar for years. The problem lies in the fact that system pop-ups are reasonably easy to spoof. A malicious app can be coded using the "UIAlertController" class and designed to look like Apple's system prompt. What's worse is that most iOS users have been "trained" to enter their passwords in these pop-ups without a second thought.
Felix Krause, the founder of mobile app publishing software fastlane, was able to demonstrate that creating an authentic looking system prompt is simple and convincing. The pop-ups look identical to those seen by iPhone and iPad users daily. The difference is these are not signing you into iTunes; they are stealing your password.
Krause did not publish the source code for his pop-ups on ethical grounds but he did submit a Radar report on the matter.
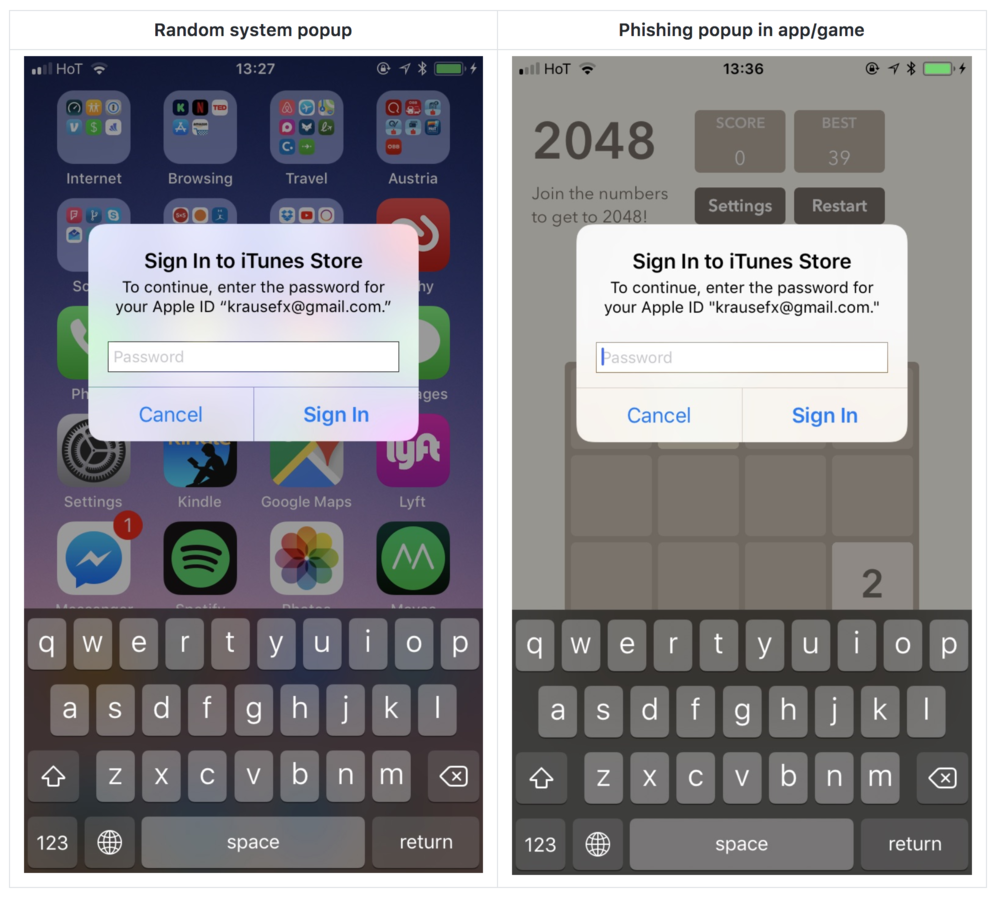
The reason this problem exists in the first place is due to all the various reasons that iOS asks for your password. Whether you are making an in-app purchase or authorizing an app to access your Game Center account, there are many times iOS is looking for your credentials outside of iTunes and the App Store.
As you can see in the images above, there is virtually no way to tell if the system dialog is authentic or not. There are even ways around having to know and produce the user's e-mail address in the dialog as seen below.
However, all is not lost. Krause has some tips for determining if a pop-up is real and how to avoid getting caught by a phishing attack.
The easiest way to tell if the prompt is from the system or the app is to hit the Home button. Krause says, "If it closes the app, and with it the dialog, then this was a phishing attack."
This works because you cannot dismiss a system dialog with the Home button; you must tap the Cancel button.
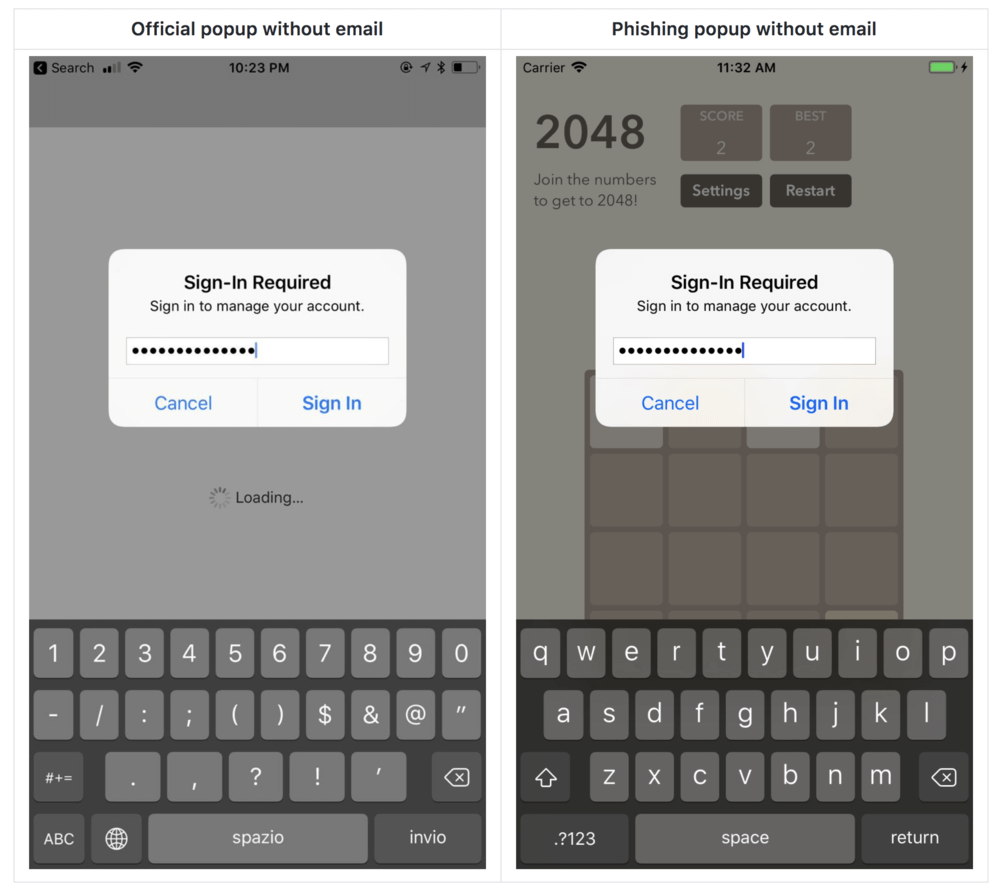
He also suggests never entering your credentials through an app. Instead, exit the app and log in to your iTunes account through Settings. Since logins stay active for several minutes, you should not receive the pop-up when opening the app again. If you do, it is likely a phishing attempt.
Krause has a couple of suggestions for Apple to correct this problem. One would be to include an app icon in the corner of dialogs to show that it is the app and not the system asking for the password.
Moreover, he thinks iOS needs to cut back on how often it requests user passwords. While it makes sense when making purchases in iTunes or the App Store, asking for passwords outside of those environments is asking for trouble. Eliminate the need for an app to ask permission and you eliminate the threat.
So far there have been no known apps that use the technique Krause describes which is somewhat surprising considering the ease at which he was able to produce fake prompts. This is in part due to Apple's strenuous app screening process but nothing is infallible. Creative hackers could still figure out ways to enable malicious code after an app has been approved.
Body images by Felix Krause