As we pointed out in our feature on High Sierra a couple of weeks ago, macOS 10.13 is not without its flaws. While the bugs we encountered were more annoying than anything else and need to be addressed in order to get a full recommendation, they weren't of a nature needing immediate attention. Since that time, a couple of more serious issues have reared their heads in Apple's latest operating system.
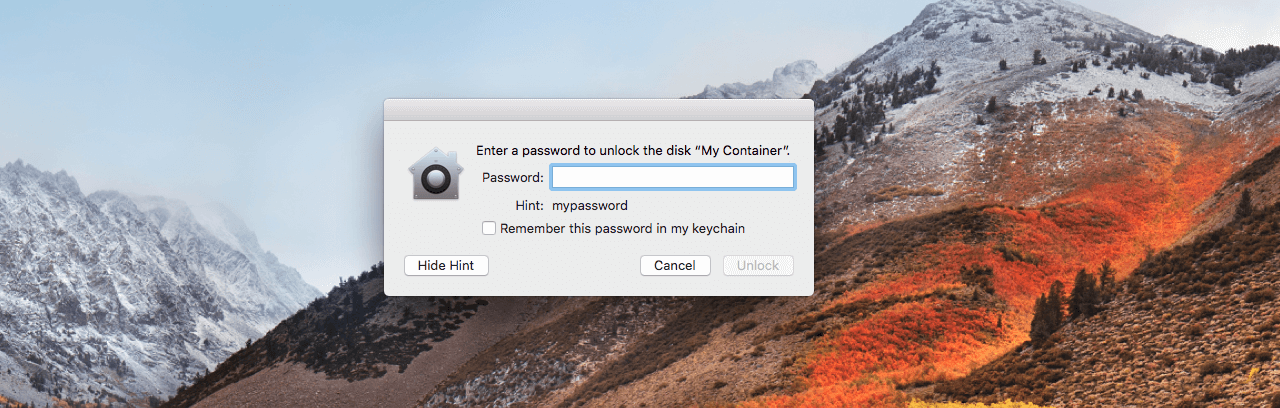
Last week Matheus Mariano, a programmer working for Leet Tech in Brazil, found a flaw in 10.13 that makes putting a password on an encrypted disk volume pointless.
The Apple File System (APFS) bug (CVE-2017-7149) happens when partitioning an SSD with Apple's Disk Utility. After setting up the password and hint for the volume, if you try to pull up the hint, it reveals the password instead as demonstrated in the video below.
If that wasn't enough, Patrick Wardle, a security researcher for Synack, recently discovered a bug with High Sherra's Keychain utility. The flaw (CVE-2017-7150) allows unsigned apps access to Keychain. This problem is serious for obvious reasons.
Apple has already addressed both issues with a patch that it released last Thursday. In the patch notes, Apple explains what was causing the problems.
"If a hint was set in Disk Utility when creating an APFS encrypted volume, the password was stored as the hint. This was addressed by clearing hint storage if the hint was the password, and by improving the logic for storing hints ... A method existed for applications to bypass the keychain access prompt with a synthetic click. This was addressed by requiring the user password when prompting for keychain access."
German programmer Felix Schwartz criticized Apple on Twitter saying, "It becomes clearer every day that Apple shipped #APFS way too early."
Developer Marco Arment shared a similar sentiment.
The biggest problem with Apple putting less effort into macOS isn't that it stagnates --- it's that they make buggier, sloppier updates. https://t.co/NUtVxeNULY
--- Marco Arment (@marcoarment) October 5, 2017
Other industry experts agree, saying that Apple has become too focused on iOS and that macOS has suffered when it comes to quality control.
Legitimately wondering of Apple accidentally shipped a pre-release version of High Sierra. So much of it is unfinished and unpolished.
--- Brian Lopez (@brianmario) September 27, 2017
If you have not installed the latest patch for macOS 10.13, you can find it on Apple's Security Update page.