Elon Musk and 116 AI experts may be worried about killer robots of the future, but many of today's machines could also pose a threat to humans because they're so easy to hack. That's the view of Seattle-based cybersecurity firm IOActive, who discovered potentially dangerous vulnerabilities in many popular home and industrial robots.
IOActive's research shows how it was able to carry out the hacks and the kind of damage they could cause. Not surprisingly, industrial robots have the potential to be extremely dangerous. Machines from Universal Robots, for example, work alongside humans and aren't confined to safety cages. IOActive was able to remotely disable their security features, meaning the huge devices wouldn't register anyone close by. "Even the smaller UR5 model is powerful enough to seriously harm a person. While running at slow speeds, their force is more than sufficient to cause a skull fracture," claims the study. They could also be programmed to do intentional harm or alter their manufacturing process.
It isn't just industrial machines that pose a threat. As was the case with the Hello Barbie and My Friend Cayla dolls, several popular home robots were found to have vulnerabilities that allowed hackers to use them for spying. Softbank's Pepper and NAO could record audio and video and transmit it to an external server, while UBTech's Alpha Series didn't encrypt personal information before storing or sending it.
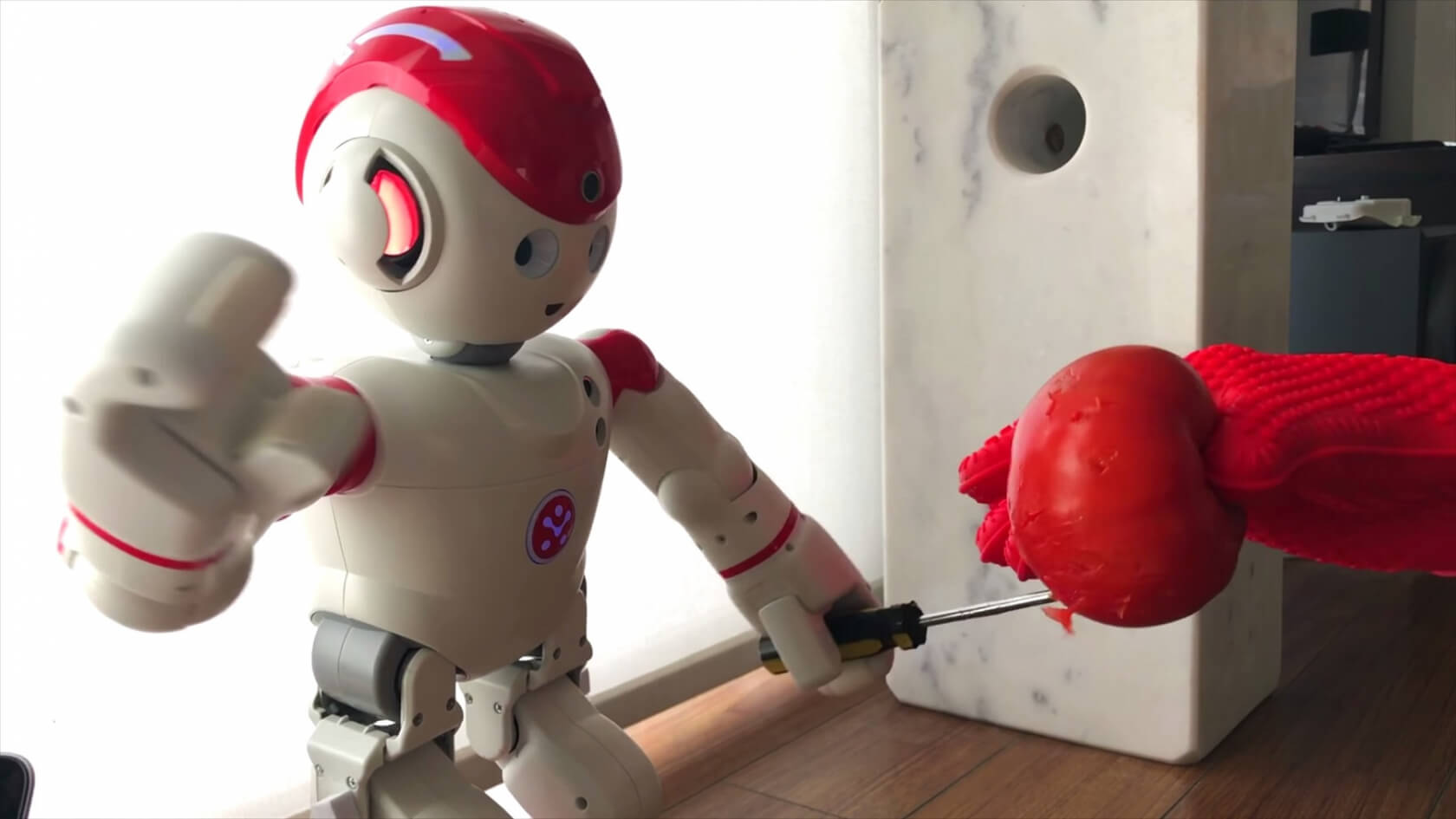
I/O interactive also showed how these consumer robots could be taken over and controlled remotely. In the video below, researchers essentially turn a UBTech Alpha 2 into horror doll Chucky (complete with voice sample) and make it repeatedly stab a tomato. While this is a humorous example that's unlikely to hurt a person, it could be potentially dangerous if used against an infant.
"Our research shows proof that even non-military robots could be weaponized to cause harm," said IO interactive's Lucas Apa. "These robots don't use bullets or explosives, but microphones, cameras, arms and legs. The difference is that they will be soon around us and we need to secure them now before it's too late."
IO interactive says it informed the companies of the flaws earlier this year, but they didn't seem interested. "We contacted all the vendors in January but sadly there's little to suggest that the 50-plus vulnerabilities we demonstrated have been fixed," Apa added. "Most vendors were not forthcoming when we contacted them in private, so going public was the only option left available to us."