Ransomware that holds your computer hostage until a fee has been paid to unlock it is pretty evil as far as nefarious code goes. Apparently, the group behind the TeslaCrypt ransomware came to that same conclusion as they've shut down the project and released the master decryption key.
As Bleeping Computer explains, an analyst at security firm ESET noticed over the past few weeks that the developers of TeslaCrypt had slowly been closing their doors. Simultaneously, some distributors have been moving their operations to a different type of ransomware.
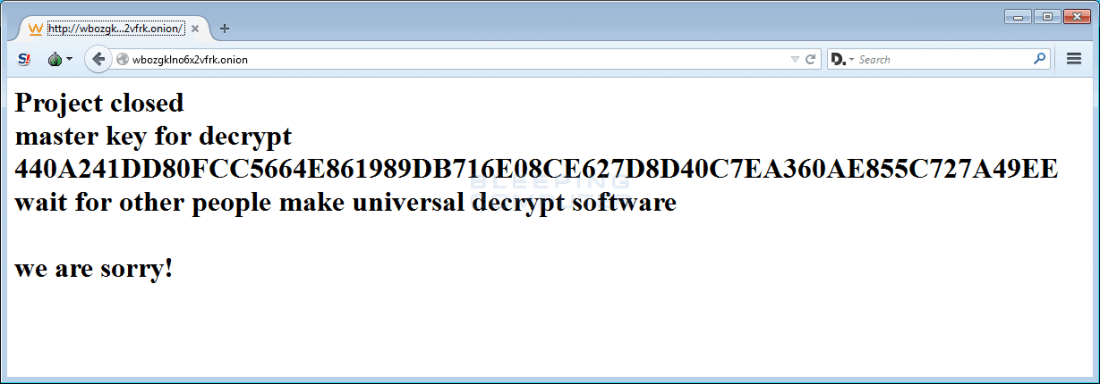
On a whim, the ESET analyst hopped on the support chat of the Tesla payment site and asked if they would release the master decryption key. Surprisingly enough, they did just that and even posted it on their now defunct payment site.
With the master key in hand, TeslaCrypt expert BloodDolly updated a program called TeslaDecoder to version 1.0. Now, the software can decrypt versions 3.0 and 4.0 of TeslaCrypt.
TeslaCrypt first surfaced in early 2015 and was unique in that it targeted gamers by encrypting data such as save files and custom maps in addition to the usual gamut of documents, photos and so on. In total, it would look for 185 different file extensions to encrypt. The only way to regain access to your files was to pay the ransom or start fresh using backups of your data.
Why TeslaCrypt's creators decided to abandon the project and publish the master key remains a mystery. Perhaps they were in a major financial pinch and needed to generate some quick cash? That of course doesn't make it right but the fact that they ultimately published the key and closed their operation does speak to their underlying character.
