A new study claims that a large portion of the most popular free apps on Google Play are highly vulnerable to malicious attacks. Security firm FireEye recently released a study suggesting that SSL vulnerabilities within these apps and the man-in-the-middle (MITM) attacks they allow for "are wreaking havoc on data security" throughout the Android ecosystem.
After analyzing the 1000 most popular free apps available on Google Play, the firm found that as many as 73% of them were highly vulnerable to MITM attacks due to poor or faulty SSL management. In a random sampling of 10,00 free applications, FireEye's data says around 60% of them were vulnerable. "These popular apps allow an attacker to intercept data exchanged between the Android device and a remote server," the company said in a blog post.
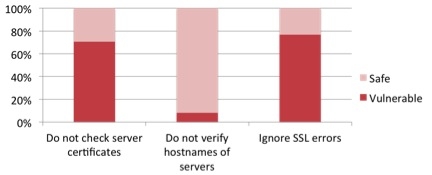
The study covered three separate SSL errors including faulty trust managers, code that mishandles SSL errors when using Webkit and when apps don't verify the remote server hostname. Trust management issues were spotted in 73% of the top 1000 free apps and 40% of the 10,000 apps FireEye looked at. Webkit errors were also quite abundant at 77% of the top 1000 free apps and around 13% of the 10,000 chosen in the study. Host verification checks seemed to be much better across the board registering in the single digits.
According to FireEye, the issues are effecting ad libraries and things of that nature as well:
"Applications may use third-party libraries to enable part of their functionality. When these libraries have baked-in vulnerabilities, they are particularly dangerous because they make all applications that use them, and frequently the devices that run them, vulnerable."
FireEye also points out that the two top advertising libraries they looked at, Flurry and Chartboost, both suffered from faulty trust management. While both of these networks have now been updated to correct the issue, the company suggests the massive number of third party apps connected to them that haven't updated yet, may still be open to attacks. Apps that in some way use Flurry's libraries, for example, "have been downloaded over 8.7 billion times," according to FireEye.
Reports suggest some of the major apps and ad networks like both of the aforementioned companies have started to introduce updates for these vulnerabilities. FireEye said it "notified the developers, who acknowledged the reported vulnerabilities and addressed them in subsequent versions of their applications." More a more technical breakdown of the company's findings head over to the official blog post.
